Start your day with intelligence. Get The OODA Daily Pulse.
Start your day with intelligence. Get The OODA Daily Pulse.
Organizations across all industry sectors (and their Board of Directors) should take a look at our recent analysis of the evolution of the upcoming SEC cybersecurity rules and CISA’s Pilot Ransomware Warning System and Pre-Ransomware Notification Initiative. The SEC will eventually provide cross-sector rules for reporting cyber incidents, while the CISA program is more of a public/private “collective intelligence” at work and more broadly collaborative. Both qualify as vital countermeasures that should be elevated to the boardroom as soon as possible and considered in a cross-functional manner across all organizations, big and small.
Running parallel to the importance of these developments at the SEC and CISA is our research (including great OODAcast conversations) on Threat Intelligence and Coordinated Vulnerability Disclosure (CVD) – related processes that can support each other and contribute to cybersecurity resilience across all technology types and sectors. Like the real danger of AI innovation at exponential speed and scale – and not adequately addressing AI governance, we hope that the 2023 National Cybersecurity Strategy becomes truly actionable and experiences a broad national implementation to address the severity of the cybersecurity challenges ahead. Threat intelligence and CVD should be central to such future efforts.
Currently, the 2023 cybersecurity strategy has no metrics associated with it, so there is no reason for anybody to act on the recommendations in the strategy document. This is a perennial problem with these strategy documents. We hold out hope that the 2023 National Cybersecurity Strategy is going to defy both the gravity and logic of the OODA Network’s collective experience that these strategy documents, historically, make a splash upon release and then gather dust in the beltway.
In that hopeful vein, we will continue to track plans by the Office of the National Cybersecurity Director (ONCD) to develop a roadmap for the National Cyber Strategy. According to Kemba Walden, the Acting National Cybersecurity Director, the roadmap will be shared with other federal agencies and partners in early summer 2023.
The roadmap will seek to address a wide scope of issues, such as:
The roadmap will also include specific metrics and milestones to measure progress and performance toward achieving the objectives of the strategy. Music to our ears.
We are also keeping an eye out for the upcoming cyber workforce strategy.
The 2023 strategy document lays out “two fundamental shifts in how the United States allocates roles, responsibilities, and resources in cyberspace,” stating that “in realizing these shifts, we aspired not just to improve our defenses, but to change those underlying dynamics that currently contravene our interests. The two fundamental shifts:
This strategy recognizes that government must use all tools of national power in a coordinated manner to protect our national security, public safety, and economic prosperity.”
We focus here on vulnerabilities as they relate to these two fundamental shifts – and the road ahead.
According to the Congressional Research Service the 2023 National Cybersecurity Strategy “recognizes vulnerability as a major cybersecurity challenge and proposes various measures to reduce vulnerability across different domains and sectors. The strategy makes clear that vulnerability is one of the key challenges that the U.S. faces in cyberspace, as malicious actors exploit weaknesses in systems, networks, devices, and data to cause harm to individuals, organizations, and national security.
The strategy also states that vulnerability reduction is one of the main objectives of the U.S. government to enhance cybersecurity and resilience. The strategy proposes several actions to achieve this objective, such as:
@DC3VDP Director, Melissa Vice, spoke recently with Martin Matishak @TheRecord_Media about its 45,000th vulnerability report and "how the Pentagon learned to love vulnerability disclosure".
— DoD Cyber Crime Center (DC3) (@DC3Forensics) March 27, 2023
Read more: https://t.co/aqdXNoEKq0 pic.twitter.com/YJdQdVcovo
MAR 2023 @DeptofDefense Vulnerability Disclosure Program #VDP @Hacker0x01 #Hackers reported on denial of service attacks against sites hosting WordPress. Read about in the #Knowledge Byte! pic.twitter.com/tazS8Z2Eaq
— DC3 VDP (@DC3VDP) April 19, 2023
Martin Matishak, a senior cybersecurity reporter for The Record, recently provided a best practices breakdown of what the Office of the National Cybersecurity Director (ONCD) could learn from DoD and how the Pentagon learned to love vulnerability disclosure – including the origins, challenges, opportunities, achievements, and implications of the program:
“Inside the national cyber strategy released last month by the Biden administration was a call for “coordinated vulnerability disclosure” across “all technology types and sectors” to help collect and share information about flaws in software, hardware, and systems nationwide. The appeal marked the latest step in the evolution of a practice that gained early acceptance in Washington in perhaps the most unlikely of places: the Department of Defense. About seven years ago, the famously bureaucratic and secretive DoD embraced the idea that people outside the department should be encouraged to spot bugs in its vast ecosystem of publicly accessible information networks and systems.” (1)
The Department of Defense’s (DoD) vulnerability disclosure program (DC3 VDP) encourages ethical hackers to report security flaws in the department’s public-facing systems and networks. Matishak traces the origins of the VDP to the success of the DoD’s first-ever bug bounty program, Hack the Pentagon, in 2016, which uncovered nearly 140 unique vulnerabilities and paid out about $100,000 in rewards – highlighting the challenges and opportunities of implementing and expanding the VDP across different components and domains of the DoD, such as the defense industrial base, classified systems, and cloud services:
“Since then, the global cybersecurity researcher community has responded enthusiastically. Last week, the department’s Cyber Crime Center (DC3) announced its vulnerability disclosure program…promises to grow as researchers are encouraged to keep ferreting out weaknesses.’We can’t do it alone. I mean, you can’t boil the ocean,’ Melissa Vice, the center’s VDP director, told The Record late last week.
Statistics and insights – on performance and impact – reflect that the DC3 VDP has:
Currently, once a proof-of-concept is submitted and checked against metrics, including the NIST National Vulnerability Database, it’s up to the Joint Force Headquarters DoD Information Network to issue the tasking order for the system owner to remediate.” (1)
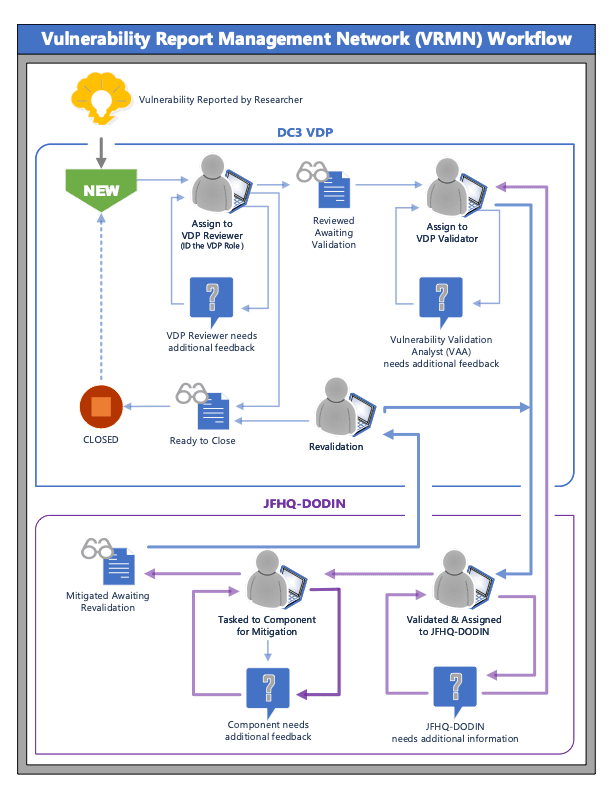
Image Source: The Record
It remains to be seen if the 2023 National Security Strategy (and the forthcoming roadmap) will be able to implement a nationwide system (along with international partners) for “coordinated vulnerability disclosure across all technology types and sectors.” A tall order – although the CISA JCDC has had some success to date.
The Records’ Matishak laid out two successful aspects of the DC3 VDP it behooves the ONCD to replicate – The White Hat Mindset and Expansion of Success at Scale:
Today, the VDP serves as a bridge between the buttoned-up DoD and the global community of ethical hackers. Unlike a bug bounty event, the program doesn’t pay out cash rewards. Instead, DC3 aims to give researchers credibility by recognizing and promoting their discoveries, via tweet or by bestowing the honorific of report of the month or report of the year when graded against the Common Vulnerability Scoring System. In a first, last year’s award went to an American, who received a swag bag, including a sweatshirt with the program’s logo and other tchotchkes from the Pentagon. (The first year’s winner lived in Ukraine, while other previous champs hailed from Kosovo and Rome.)
The August 2022 hacker of the month, Sudhanshu Rajbhar, said he prefers the cash rewards of the bug bounty events, but he also appreciates the ability to safely report bugs through the VDP. He said that some hackers who once drew attention for defacing DOD websites now submit bugs to the official program. “Their team is mature and very professional, and understands the impact of the reported bugs. Overall it has been a great experience working with them,” said Rajbhar, a university student in India who uses the Twitter handle @sudhanshur705.
“You don’t need any degree or any qualification for this, all you need is a hacker mindset and a never-ending thirst for knowledge,” Rajbhar said.
[Melissa Vice, the DC3 VDP Director] said the center is looking to boost the program’s “scalability” through new partnerships in the research community and academia, as well as potentially expanding on two recent pilot programs that proved successful.
The first was a yearlong, voluntary effort that scrubbed a sliver of the public networks belonging to the 300,000-plus contractors in the defense industrial base — a favorite target of foreign hackers looking to pilfer national security secrets and intellectual property — and turned up more than 400 flaws.
“I think there are really strong indicators that we will see a resurgence of this type of program coming forward or pilot 2.0,” according to Vice.
The second was an event by HackerOne under the auspices of the VDP that saw hackers dig into DoD networks for cash.
“VDPs are a timed process, you only get credit for the very first one to initiate it and submit it into the actual, so you can’t sit on these,” Vice explained. Traditional bug bounty programs, by contrast, are “very targeted and they’re by invitation only. It’s a very different crowd set that you’re speaking to, in a VDP versus a bug bounty, but we can see the goodness of having those two conjoined.”
Meanwhile, the center continues to field calls from other agencies (the Cybersecurity and Infrastructure Security Agency in 2020 ordered civilian entities to create them), states and foreign governments asking for tips on how to set up their own programs and weed out flaws in the networks.
Chris Lynch, the founding director of the Pentagon’s Defense Digital Service…and now the co-founder and chief executive officer at software contractor Rebellion Defense, marveled over the program’s longevity and impact through Washington and beyond. “It’s amazing,” he said. “To see the VDP take off, get continued funding and support and be successful, it’s just a reminder that at the end of the day, this notion of you know, security through obscurity — and keeping our head in the sand around our vulnerabilities and weaknesses — it’s just not the right approach.” (1)
https://oodaloop.com/oodacast/2023/03/17/adam-shostack-on-cybersecurity-and-what-every-engineer-should-learn-from-star-wars/
https://oodaloop.com/archive/2022/01/28/charity-wright-on-chinas-digital-colonialism/
https://oodaloop.com/archive/2023/03/17/what-corporate-directors-need-to-know-about-coming-sec-cybersecurity-rules/
https://oodaloop.com/archive/2023/04/04/cisas-pilot-ransomware-warning-system-and-pre-ransomware-notification-initiative/
https://oodaloop.com/archive/2023/03/03/the-ooda-network-on-the-2023-national-cybersecurity-strategy/
https://oodaloop.com/archive/2023/03/06/the-missing-piece-of-the-national-cybersecurity-strategy/
https://oodaloop.com/archive/2023/03/26/march-2023-ooda-network-member-meeting-tackled-strategy-misinforming-regulation-systemic-failure-and-the-emergence-of-new-risks/
https://oodaloop.com/archive/2023/03/21/how-to-manage-cyber-risk-as-a-board-director/
https://oodaloop.com/archive/2023/01/27/sophos-kristin-del-rosso-on-the-us-national-vulnerability-database-nvd-and-the-chinese-nvd-cnnvd/
https://oodaloop.com/archive/2023/02/07/a-conversation-with-ooda-network-expert-kristin-del-rosso-on-cybersecurity-and-national-vulnerability-database-research/
https://oodaloop.com/archive/2022/10/12/will-expansion-of-the-vulnerabilities-equities-process-vep-strengthen-national-security-and-coalition-collaboration/