Start your day with intelligence. Get The OODA Daily Pulse.
Start your day with intelligence. Get The OODA Daily Pulse.
The ODNI’s Counterintelligence Center (the National Counterintelligence and Security Center (NCSC) and the FBI and USAF have issued a joint bulletin designed to raise awareness of threats to the U.S. space industry.
This bulletin conveys important information that should be read and acted upon by any in the U.S. space industry. The government is doing us all a huge service by providing this warning.
We note, however, that the government recommendations on what to do about the threat fall short. There are some big recommendations the government should have made but didn’t, perhaps because they don’t really know how business works or perhaps they are hamstrung by bureaucracy. We discuss this more in our recommendations at the bottom of this post.
Before getting to recommendations, review the text from the bulletin here:
The Threat
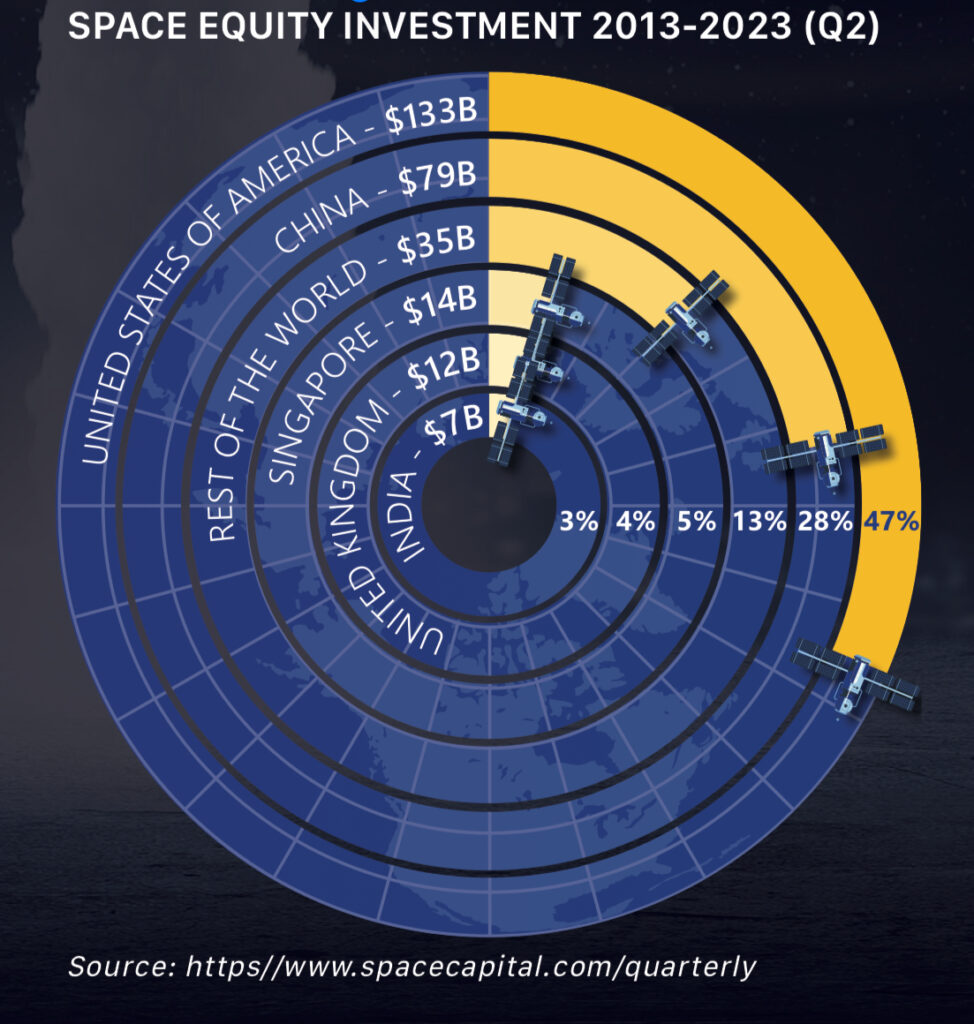
According to US financial sector estimates, the global space economy is projected to grow from $469 billion in 2021 to more than $1 trillion by 2030. The United States is the main driver of this growth through its role as a global leader in space investment, research, innovation, and production. Space is fundamental to every aspect of our society, including emergency services, energy, financial services, telecommunications, transportation, and food and agriculture. All rely on space services to operate.
Foreign intelligence entities (FIEs) recognize the importance of the commercial space industry to the US economy and national security, including the growing dependence of critical infrastructure on space-based assets. They see US space-related innovation and assets as potential threats as well as valuable opportunities to acquire vital technologies and expertise. FIEs use cyberattacks, strategic investment (including joint ventures and acquisitions), the targeting of key supply chain nodes, and other techniques to gain access to the US space industry.
FIE efforts to target and exploit the US space industry can harm US commercial firms and broader US national and economic security in several ways:
Global Competition
National Security
Economic Security
Indicators
Your employees, contractors, and suppliers are vital to protecting your organization. Be aware of the following indicators and other potential signs of FIEs targeting you.
Mitigations:
You are not helpless in the face of FIE threats to your organization.
Reporting Incidents:
If you believe your company’s intellectual property has been targeted or is at risk of compromise, contact the Private Sector Coordinator at your local FBI Field Office:
https://www.fbi.gov/contact-us/field-offices
You can also submit a tip to the Department of the Air Force Office of Special Investigations at:
https://www.osi.af.mil/Submit-a-Tip/
More Recommendations From OODA:
We love this report for what it does that no one else can. It gives insights from the perspective of our nation’s intelligence and law enforcement professionals and makes it clear this is a serious threat. And it provides general recommendations relevant to almost any firm in the US Space Industry.
But some major recommendations were left out. We assume this is because the government is in a hard position and cannot take action that might make it seem like they are making business recommendations or endorsing work with any particular group. We are not handcuffed by those problems so will tell you what we think.
Besides the smart recommendations provided by the government we strongly recommend and U.S. space firms:
Members of the OODA expert network continuously track best practices for policy, procedures, technology and governance related to cyber defense. We work directly defending enterprises in cyber defense and maintain an always up to date list of actions in a form designed to help any organization stay as agile as possible in the face of dynamic adversaries.
Enterprise technologists use the term “Zero Trust” to describe an evolving set of cybersecurity approaches that move defenses from static attempts to block adversaries to more comprehensive measures that improve enterprise performance while improving security. When the approaches of Zero Trust are applied to an enterprise infrastructure and workflows, the cost of security can be better managed and the delivery of functionality to end users increased. Security resources are matched to risk. Functionality, security and productivity all go up.
Over the past four years there has been an avalanche of new Zero Trust products. However during the same period there has been no measurable reduction in cyber breaches. Zero Trust is a concept where an organization has Zero Trust in a specific individual, supplier or technology that is the source of their cyber risk. One needs to have Zero Trust in something and then act to neutralize that risk. Thus buying a Zero Trust product makes no sense unless it is deployed as a countermeasure to specific cyber risk. Buying products should be the last step taken not the first. To help enterprises benefit from Zero Trust concepts here is a modified OODA loop type process to guide your strategy development and execution.