Start your day with intelligence. Get The OODA Daily Pulse.
Start your day with intelligence. Get The OODA Daily Pulse.
Not much unlike 2021 (and actually quantifiably worse), 2022 was marked by security professionals reacting to threats, incidents, and vulnerabilities of a constant, unrelenting frequency, volume, and scale. At the end of 2021, in a series of posts entitled The New Normal, we provided case studies of a few of the major cyber incidents which, cumulatively by the end of last year, made it abundantly clear that we were on terra incognito in a way which would clearly carry over into 2022. Also included in our analysis at the time were new threat vectors that were met by new corporate, governmental, and legal mechanisms for response to cyber incidents of all kinds (cyber fraud, crypto theft, data breach, ransomware, etc.) – a trend in this ecosystem which has continued over the course of 2022 as well.
“…there is more crime being done in the traditional financial system than in the crypto ecosystem right now…”
Over the past several years, there has also been a rapid emergence of companies, projects, and initiatives in what is broadly categorized as Web3, of which the cybersecurity implications were unclear to us until – while monitoring that rapid innovation in 2022 – the OODA research team noticed a disproportionately high number of cybersecurity incidents that have the potential to negatively impact the Web3 ecosystem. Massive, headline-grabbing cryptocurrency security failures – followed by equally massive cyber fraud and cryptocurrency theft – prompted the creation of the OODA Cryptocurrency Incident Database in February 2022.
As our OODA Loop Global Crypto and Digital Currency Initiatives Series demonstrate, we take the long view on the global adoption rate of crypto as a stable currency standard capable of challenging the historical dominance of the U.S. dollar: the series is a compilation of posts on crypto and digital currency initiatives from around the globe, all of which are officially sanctioned to enhance national competitive advantage (in the event crypto overtakes the US dollar as the global reserve currency). The cumulative adoption rate of state-sanctioned crypto and digital currency legalization and regulation may still (against the odds of security issues and the vagaries of early efforts at regulation) propel this innovative system for value creation, storage, transfer, and exchange as an official global currency standard. As OODA CEO Matt Devost adds: “I thought it was telling when MobileCoin, which is linked to Signal, decided not to operate in the United States at all. If you wanted to participate in the economics around a token that was tied to Signal – which I use every single day- you couldn’t do it as a U.S.-based entity. You had to move crypto assets offshore.”
We remain bullish long term on cryptocurrency and bitcoin on a relative basis to traditional financial systems, based on the following data points which get lost in the irrational exuberance and unintended consequences currently plaguing crypto: Laura Shin, a prominent journalist in the space, recently reported that “for 2021, the last complete year of crime data, Chainanalysis reported that 0.15% of crypto transactions are related to illicit activity; while the World Bank reported that, in the traditional financial system, that number is more like 2 to 5%. So there is more crime being done in the traditional financial system than in the crypto ecosystem right now. I know that goes against the general perception…but Chainanalysis is a trusted source in the industry and by the government.” (1) Matt elaborates on the comparison to the traditional financial system:
“The fraud that is happening in FTX is not something that is unique to the crypto space. We have Greensill Capital. We have 1MDB. We have these other instances where there’s been incredible large-scale fraud linked to very significant players. FTX should have been doing better due diligence, but I think we do a disservice if we track just the fraud in the crypto space without recognizing that large-scale, multi-billion-dollar fraud is happening in these other ecosystems as well. FTX, for me, is first and foremost, a question of the fact that I don’t like seeing people get hurt financially. I think the fact that these systems are crumbling will allow us to create new solutions and apply scrutiny – because there was a lot of shady behavior by shady people, but also by people who were not necessarily shady, but were operating out in the open with some of these investments and some of these schemes. So I see it as a net positive overall that we are going through this churn. And I do believe that the underlying technologies have a lot of promise in the future.”
“…these continuous, successful outcomes vis-à-vis the protection of U.S. critical, physical, industrial and cyber infrastructure are not some happy accident.”
2022, however, has not only been about cybersecurity as it relates to the cryptocurrency marketplace meltdown and enterprise cybersecurity. In as much as our 2022 OODA Loop “Year-end Review” series of posts is a tapestry, the sheer size of the cybersecurity threat and attack surface also has threads woven into the federal government, geopolitical risk, and technology. Like the DHS track record of not a single kinetic attack by foreign adversaries on U.S. soil since 9/11, so too there has not been a significant cyberattack on U.S.-based information and communication technologies (ICT), physical security, critical infrastructure or industrial control systems (ICS) at the scale of the predicted “big one” based on the “escalate to de-escalate” cyber doctrine of the Kremlin since invading Ukraine. Or from Iran, China, or North Korea for that matter. All the while, the global weaponization of the IT supply chain escalates, as illustrated by the recent Leviathan attacks and kinetic naval intervention in the South China Sea.
You do not have to have a high-level clearance to know that these continuous, successful outcomes vis-à-vis the protection of U.S. critical, physical, industrial, and cyberinfrastructure are not some happy accident. It is work, with people behind it – and a job well done in 2022. What’s more, markets do not like uncertainty and leadership matters: the same USG acronym organizations that were the tip of the federal spear for these cybersecurity successes in 2022 were also in charge of the critical infrastructure which provided for another fair and secure election process for the mid-terms in 2022. In fact, Gen. Paul Nakasone recently discussed publicly the extent of Cyber Command offensive operations to protect the midterm elections.
…what role will exponential disruption and emerging technologies play in the transformation of cybersecurity?
It is in this hard-fought context of a still functioning democracy that the free market flourishes, sparking innovation, sorting out winners and losers, and creating abundance and prosperity. And yet, the cybersecurity innovation marketplace still cannot get its footing: 2022 marks another year of a lack of innovation and a dearth of new solutions-driven platforms, innovative business model generation, and value creation. So much so that Matt earlier this month, when he released his Top 10 Security, Technology, and Business Books of 2022, noted: “With the launch of the Hack Factory this year, I’ve been very focused on business, building technologies, and investing style books. As a result, that is a major theme for this year. Noticeably absent are books on Blockchain/Cryptocurrencies as that industry is in the middle of a creative destruction phase, and I continue to view cybersecurity as being stuck in a ‘Cyber Winter’.”
By the time of the FTX crypto maelstrom, Matt had upped his description of the crypto marketplace from the familiar Schumpeter-inspired ‘creative destruction’ – a familiar market activity that is historically a precursor to the eventual M&A consolidation of a subsector of innovation- to “destruction destruction” (which puts us, once again, on new terrain as 2022 draws to a close). The FTX and Binance debacles have set the tone early for 2023 (a year that will undoubtedly be filled with headlines about the inevitable correction in the marketplace, including court cases to track throughout the year).
As for the cybersecurity community and the state of innovation? We have been tracking the fusion of operational technologies and IT, especially as it relates to the increasing attacks and threat of large-scale attacks directed at critical infrastructure and industrial control systems by state and non-state actors alike. This threat vector has spurred on newfound innovation and collaboration in some heavy industrial sectors where none previously existed (necessity the mother of invention). But, overall in 2022, the Cyber Winter continued and the song remains the same:
“There will be a shift in this landscape in 2023…as CISA moves from ‘partner’ to ‘regulatory enforcer’ [with] a complex cyber incident reporting mandate.”
Rob Joyce and Jen Easterly continue their tenure at the National Security Agency’s (NSA) Cybersecurity Directorate and The Cybersecurity and Infrastructure Security Agency (CISA), respectively, while Chris Inglis resigned recently as National Cyber Director. Gen. Paul Nakasone also continues to lead both the National Security Agency and CYBERCOM, as the 2022 review of the NSA and Cyber Command leadership structure ended without an official recommendation.
Cybersecurity efforts by the federal government and corporate IT continued in earnest by way of the CISA Cybersecurity Advisory Committee (CSAC), which meets quarterly, and the Joint Cyber Defense Collaborative (JCDC). All the while, the private sector continued to ramp up the sophistication of its cybersecurity efforts (in what is historically a global IT supply chain predominantly managed and operated by high-technology companies, not government agencies). There will be a shift in this landscape in 2023, however, as CISA moves from ‘partner’ to ‘regulatory enforcer’ as the agency takes on a complex cyber incident reporting mandate. Hovering over the entire cybersecurity discipline and marketplace: the information threat vectors of misinformation, disinformation, information disorder, and cyberwar threats from state and non-state actors alike.
Cybersecurity headlines of note in 2022 included:
CISA Releases Voluntary Cross-Sector Cybersecurity Performance Goals: In July 2021, President Biden signed a National Security Memorandum on Improving Cybersecurity for Critical Infrastructure Control Systems. This memorandum required CISA, in coordination with the National Institute of Standards and Technology (NIST) and the interagency community, to develop baseline cybersecurity performance goals that are consistent across all critical infrastructure sectors. These voluntary cross-sector Cybersecurity Performance Goals (CPGs) are intended to help establish a common set of fundamental cybersecurity practices for critical infrastructure and especially help small- and medium-sized organizations kickstart their cybersecurity efforts.
Strategic Plan for 2023-2025 Announced at 4th Meeting of the CISA Cybersecurity Advisory Committee: The fourth meeting of the Cybersecurity and Infrastructure Security Agency (CISA) Cybersecurity Advisory Committee (CSAC) was held in September 2022. Opening remarks were addressed to the committee by Ms. Megan Tsuyi, CISA CSAC Designated Federal Officer, The Honorable Jen Easterly, Director, CISA, Mr. Tom Fanning, CSAC Chair, and Mr. Ron Green, CSAC Vice Chair. – including the announcement and review of the 2023-2025 CISA Strategic Plan.
The CISA CSAC: Cognitive Infrastructure Research and Election Public Messaging: The Cybersecurity and Infrastructure Security Agency (CISA) continues to model an operational structure with an effective public/private partnership component that yields actionable results. The latest success is the evolution of the CISA Cybersecurity Advisory Committee (CSAC which meets quarterly) and its subcommittees, specifically the time-sensitive work of the Protecting Critical Infrastructure from Misinformation and Disinformation (MDM) Subcommittee. Following is the anatomy of a CSAC subcommittee, including the mission statement formulated in December 2021, followed by the subcommittee’s quarterly updates, reports, and recommendations. The case study concludes with the recently released public service announcement from the FBI and CISA – which demonstrates the value and impact of the work of the subcommittee since December 2021.
CISA Granted Subpoena Power as Cyber Incident Reporting Bill Signed into Law: There are so many important headlines we do not want to get lost ‘below the fold’ for our membership, and this update is one of those headlines. On March 2nd, the Senate unanimously passed the Strengthening American Cybersecurity Act. A vital piece of the consolidated legislation was a cyber incident reporting bill. On March 11th, lawmakers approved the bill as part of a sweeping $1.5 trillion government funding deal. The House passed the legislation earlier in the week. On March 15th, all these efforts came to fruition as President Biden signed the cyber incident reporting bill into law.
Cyber Incident Reporting Rule for Critical Infrastructure Approved by U.S. Senate: In March, hours before the State of the Union address, the Senate unanimously passed the Strengthening American Cybersecurity Act, which is actually various bills that have now been made into one piece of legislation. Months ago, the measures had previously been removed from the annual defense policy bill.
FBI AND CISA Public Service Announcement: Malicious Cyber Activity Against Election Infrastructure Unlikely to Disrupt or Prevent Voting: The Federal Bureau of Investigation (FBI) and CISA have published a joint public service announcement that: Describes methods that foreign actors use to spread and amplify false information—including reports of alleged malicious cyber activity—in attempts to undermine trust in election infrastructure; and confirms “the FBI and CISA have no information suggesting any cyber activity against U.S. election infrastructure has impacted the accuracy of voter registration information, prevented a registered voter from casting a ballot or compromised the integrity of any ballots cast.” The PSA also describes the extensive safeguards in place to protect election infrastructure and includes recommendations to assist the public in finding trustworthy sources of election-related information.
The FBI and CISA on Information Manipulation Tactics for 2022 Midterm Elections: The Federal Bureau of Investigation (FBI) and CISA have published a joint public service announcement that: Describes methods that foreign actors use to spread and amplify false information—including reports of alleged malicious cyber activity—in attempts to undermine trust in election infrastructure; and confirms “the FBI and CISA have no information suggesting any cyber activity against U.S. election infrastructure has impacted the accuracy of voter registration information, prevented a registered voter from casting a ballot or compromised the integrity of any ballots cast.” The PSA also describes the extensive safeguards in place to protect election infrastructure and includes recommendations to assist the public in understanding how to find trustworthy sources of election-related information.
CISA Insights Bulletin Urges U.S. Preparation for Data-wiping Attacks: Recent data-wiping attacks, targeting Ukrainian government agencies and businesses, prompted the release of a CISA Insights Bulletin urging U.S. organizations to strengthen their cybersecurity defenses. In what felt like coordinated attacks last Friday, the data-wiping malware (masquerading as ransomware) hit Ukrainian government organizations and was quickly followed by an aggressive unattributed cyber attack on Ukrainian government sites.
See below for some of the noteworthy events from and critical perspectives on the last year in cybersecurity.
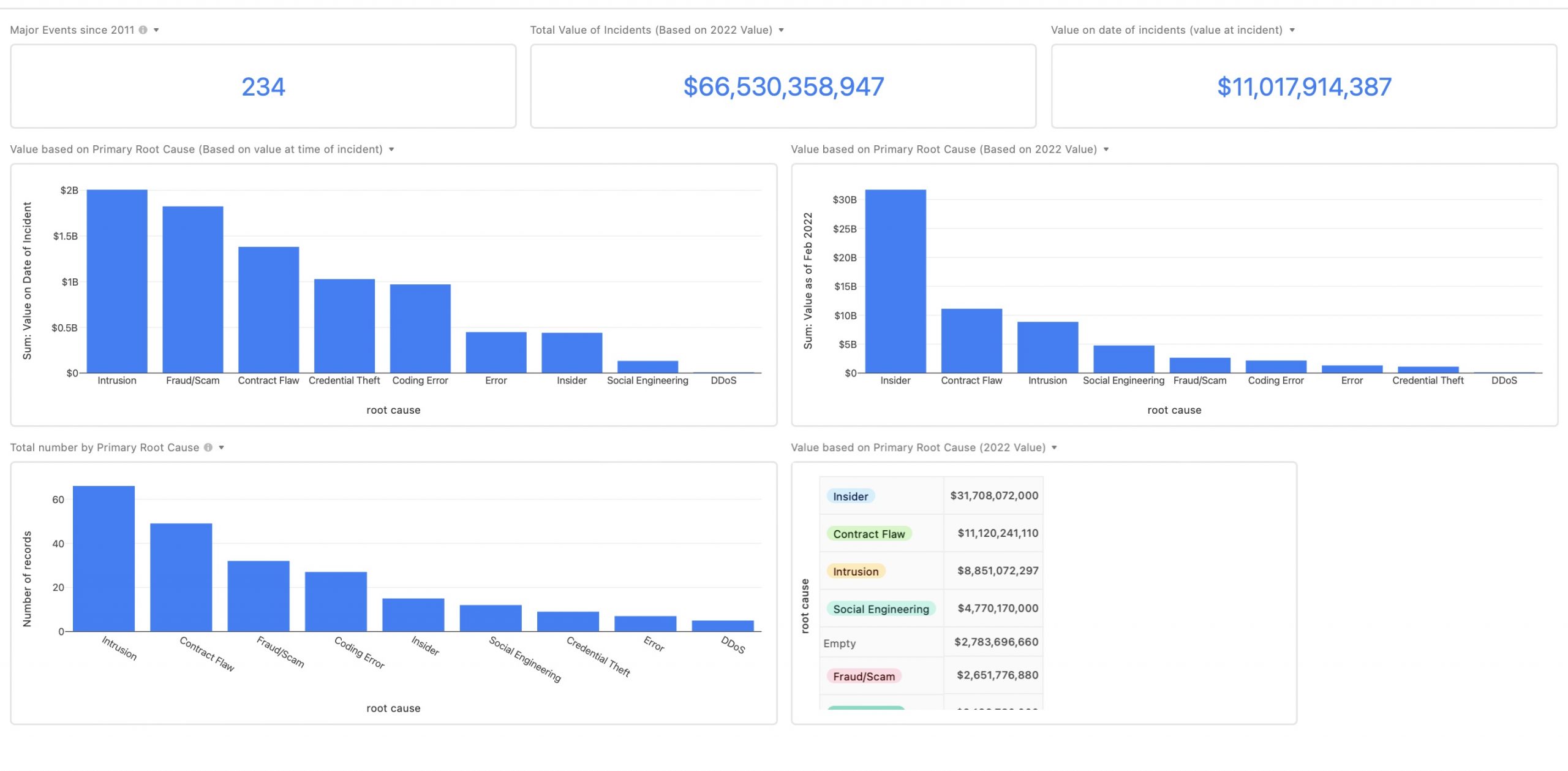
OODA has compiled a Web3 incident database based on our research to categorize what compromises are taking place as well as document the cyberattack root causes. Tracking root causes provides insights into how innovators can create robust cyber risk management approaches and reduce the potential for consequential attacks.
Reviewing the database leads to several conclusions on the need for improved risk mitigation. We capture many of our recommendations in this report on Web3 Security.
Below is a summary graphic and then direct access to the database.
Click for the live version:
 OODA members can search the database of incidents below. Click on any card to expand for more details.
OODA members can search the database of incidents below. Click on any card to expand for more details.
January 2022
February
March
April
May
June
July
August
September
October
November
December
https://oodaloop.com/archive/2022/10/28/cybersecurity-is-an-infinite-game/
https://oodaloop.com/archive/2022/06/20/opportunities-for-advantage-mobilizing-innovation-through-the-dhs-science-and-technology-directorate/
https://oodaloop.com/archive/2022/10/16/ooda-network-member-junaid-islam-on-global-cyber-risk-weaponized-it-supply-chains-and-the-enterprise/
https://oodaloop.com/archive/2022/10/13/ongoing-efforts-to-combat-information-disorder-and-strengthen-our-cognitive-infrastructure/
https://oodaloop.com/ooda-original/2022/10/21/shields-up/
https://oodaloop.com/archive/2022/03/18/lifelong-hacker-and-experienced-security-executive-alyssa-miller-author-of-cybersecurity-career-guide/
https://oodaloop.com/archive/2022/03/04/chris-butler-on-the-value-of-adversarial-thinking-in-product-design-and-management/
https://oodaloop.com/archive/2022/01/07/ben-dubow-on-detecting-and-countering-malign-influence-operations/
https://oodaloop.com/archive/2022/02/11/simon-clark-on-investigating-the-key-man-and-a-billion-dollar-fraud/
It should go without saying that tracking threats are critical to inform your actions. This includes reading our OODA Daily Pulse, which will give you insights into the nature of the threat and risks to business operations.
Use OODA Loop to improve your decision-making in any competitive endeavor. Explore OODA Loop
The greatest determinant of your success will be the quality of your decisions. We examine frameworks for understanding and reducing risk while enabling opportunities. Topics include Black Swans, Gray Rhinos, Foresight, Strategy, Strategies, Business Intelligence, and Intelligent Enterprises. Leadership in the modern age is also a key topic in this domain. Explore Decision Intelligence
We track the rapidly changing world of technology with a focus on what leaders need to know to improve decision-making. The future of tech is being created now and we provide insights that enable optimized action based on the future of tech. We provide deep insights into Artificial Intelligence, Machine Learning, Cloud Computing, Quantum Computing, Security Technology, and Space Technology. Explore Disruptive/Exponential Tech
Security and resiliency topics include geopolitical and cyber risk, cyber conflict, cyber diplomacy, cybersecurity, nation-state conflict, non-nation-state conflict, global health, international crime, supply chain, and terrorism. Explore Security and Resiliency
The OODA community includes a broad group of decision-makers, analysts, entrepreneurs, government leaders, and tech creators. Interact with and learn from your peers via online monthly meetings, OODA Salons, the OODAcast, in-person conferences, and an online forum. For the most sensitive discussions interact with executive leaders via a closed Wickr channel. The community also has access to a member-only video library. Explore The OODA Community.