Start your day with intelligence. Get The OODA Daily Pulse.
Start your day with intelligence. Get The OODA Daily Pulse.
With 3 Billion Facebook users worldwide, the strategic marketing the company has ginned up about the impending arrival of the metaverse, the ongoing impact of -mis, disinformation, information disorder, and the ongoing hobbling of the U.S. cognitive infrastructure – Meta matters.
The following post is organized around five driving forces in ‘Big Tech’ (and how they have manifested in or had a recent impact on the Meta):
One tech commentator frames the current technology sector layoff spree as an extension of the permission structure created by Elon Musk with the layoffs at Twitter: “The biggest impact in business this year, is not AI, it is not supply chains, it is the sonic boom heard around the world: Elon Musk taking Twitter from 7,500 employees down to a 1000, and he did it in like 6 to 9 months. I do not think that has ever been done at a company that was break even and not in immediate distress. I have never seen….when he came into the company, it was losing money on a cash flow basis, but it was break even-ish. There was not a burning platform other than the debt he took on. I think it is a minimum viable product” (1). He goes on to characterize the macro forces at work in the tech sector workforce:
“In the information economy, the balance between capital and labor likely swung too far toward labor. Wall Street bankers decided they could do Zoom meetings and proofread deal docs at Starbucks. Big Tech was particularly under the gun, offering not just larger and larger pay packages, but a raft of perks (e.g. valet parking, red-wine-braised short ribs, and free blankets), while loading up on employees — all of which created upward pressure on wage inflation.
Then things changed. First, Apple added opt-in tracking to iOS, threatening the ad-supported ecosystem. Then, the impact of less free money and a return to supply chain normalcy freed up the natural business cycle, and companies (and their shareholders) realized they couldn’t keep increasing their headcount 20% each year. The balance between capital and labor in the growth economy has reverted. Tellingly, these layoffs have largely been confined to tech, a relatively small portion of the economy the media covers obsessively. Perception bests reality when headlines report a five-figure layoff every week, and nobody does the math on the broader employment picture. One of the great externalities in society is an ad-supported ecosystem that turns attention to capital, resulting in a catastrophizing of all media. (2)
Source: Disinflation | No Mercy / No Malice (profgalloway.com)
Zuckerberg framed the latest cuts as being part of Meta’s broader “year of efficiency” campaign
Meta’s workforce ballooned in recent years as the Facebook parent company signaled its ambitions for the metaverse—but recent moves suggest that it is feeling the sting of changing tech trends and rough market conditions. The company…announced another round of layoffs, one day after saying that it was “winding down” support for NFTs. Co-founder and CEO Mark Zuckerberg wrote in a post today that Meta will shed about 10,000 further employees in the months ahead across multiple waves, as well as close about 5,000 current listings for open positions.
The moves will affect its recruiting department…its tech groups in April…and business groups in May. Meta previously laid off about 11,000 employees in November [2022], representing about 13% of its workforce at the time, per CNBC.
As of December 31, 2022, Meta reported having a headcount of 86,482 people across all divisions—a 20% jump from the year prior—but said that the tally still included most of the people included in the November layoffs. Zuckerberg framed the latest cuts as being part of Meta’s broader “year of efficiency” campaign, in which the social media giant attempts to continue ahead with a leaner team while flattening its organizational structure, “canceling lower-priority projects,” and optimizing tools and processes across the company.
Two segues into the generative AI gestalt in the tech sector- and Meta’s position within it. The first is a macro view of AI-based job destruction or creation:
“The chaser dropped on November 30, when every knowledge worker (reportedly) met their replacement: ChatGPT. With more than 30 million users, ChatGPT is arguably the fastest-growing product in history. (The iPhone sold 6 million units in its first year; granted, they cost $499 each and ChatGPT is free.) I used to say about WFH that if your job can be done from Boulder, it can be done from Bangalore. Well, in 2023, the new Bangalore may be ChatGPT. Inflation is about supply, demand, and psychology, and the psychology of ChatGPT is that it may not be a good time to quit your job. Unless, of course, you’re joining an AI startup. History tells us the innovation in AI will likely create more jobs than it destroys.” (2)
The second – AI as a priority at Meta, which “has increasingly pivoted its messaging towards the renewed fervor around artificial intelligence (AI) thanks to the success of rival OpenAI’s ChatGPT. Indeed, Zuckerberg’s post today mentions AI ahead of the metaverse among technologies that Meta is focused on. ‘Our single largest investment is in advancing AI and building it into every one of our products,’ he wrote. ‘Our leading work building the metaverse and shaping the next generation of computing platforms also remains central to defining the future of social connection.’” In Meta’s Q4 2022 earnings call on February 1, Zuckerberg said that the “major technological waves driving our roadmap are AI today and over the longer term the metaverse,” adding that the firm’s “priorities haven’t changed since last year.” (3)
The new ImageBind model combines text, audio, visual, movement, thermal, and depth data. It’s only a research project but shows how future AI models could be able to generate multisensory content.
Meta “announced a new open-source AI model that links together multiple streams of data, including text, audio, visual data, temperature, and movement readings. The model is only a research project at this point, with no immediate consumer or practical applications, but it points to a future of generative AI systems that can create immersive, multisensory experiences and shows that Meta continues to share AI research at a time when rivals like OpenAI and Google have become increasingly secretive.
The core concept of the research is linking together multiple types of data into a single multidimensional index (or “embedding space,” to use AI parlance). This idea may seem a little abstract, but it’s this same concept that underpins the recent boom in generative AI.
Multimodal AI models are the heart of the generative AI boom
For example, AI image generators like DALL-E, Stable Diffusion, and Midjourney all rely on systems that link together text and images during the training stage. They look for patterns in visual data while connecting that information to descriptions of the images. That’s what then enables these systems to generate pictures that follow users’ text inputs. The same is true of many AI tools that generate video or audio in the same way.
Meta says that its model, ImageBind, is the first to combine six types of data into a single embedding space. The six types of data included in the model are: visual (in the form of both image and video); thermal (infrared images); text; audio; depth information; and — most intriguing of all — movement readings generated by an inertial measuring unit, or IMU. (IMUs are found in phones and smartwatches, where they’re used for a range of tasks, from switching a phone from landscape to portrait to distinguishing between different types of physical activity.)”
The idea is that future AI systems will be able to cross-reference this data in the same way that current AI systems do for text inputs. Imagine, for example, a futuristic virtual reality device that not only generates audio and visual input but also your environment and movement on a physical stage. You might ask it to emulate a long sea voyage, and it would not only place you on a ship with the noise of the waves in the background but also the rocking of the deck under your feet and the cool breeze of the ocean air.” (4)
Speaking of ChatGPT as it relates to future cybersecurity threats for social media platforms:
“Security researchers have identified another threat leveraging the popularity of ChatGPT to spread malware and conduct nefarious activities. The latest attack is a fraudulent Chrome extension masquerading as ChatGPT. The threat actors behind the application forked a legitimate open source extension and added malicious code to steal Facebook session cookies from victims. The threat actors behind the extension have also created malicious sponsored search engine results in order to promote the application.
The fraudulent extension is reportedly difficult to distinguish from the legitimate version, security researchers state. The malicious code steals cookies and encrypts and exfiltrates them, allowing threat actors to obtain on-demand access to compromised accounts. In this instance, the threat actors change the log in details and lock the user out.” (5)
“A Chinese disinformation network operating fictitious employee personas across the internet used a front company in London to recruit content creators and translators around the world, according to Meta. In a report published [in May], Meta revealed it had removed more than 100 accounts on Facebook and dozens on Instagram connected to the operation targeting “multiple internet services,” including almost all of the major social media platforms. The operation used a company called London New Europe Media, registered to an address on the upmarket Kensington High Street, that attempted to recruit real people to help it produce content. It is not clear how many people it ultimately recruited.
London New Europe Media also “tried to engage individuals to record English-language videos scripted by the network,” in one case leading to a recording criticizing the United States being posted on YouTube, said Meta. While the actual operators of this network attempted to conceal their identities, Meta said its investigation had “found links to individuals in China associated with Xi’an Tainwendian Network Technology, an information technology company.” The London operation created fake personas impersonating companies and institutions in the U.S. and EU, initially making posts mimicking the entity before switching to publishing negative commentary about Uyghur activists and critics of the Chinese state.” (6)
Released May 3rd, By Ben Nimmo, Global Threat Intelligence Lead, and Nathaniel Gleicher, Head of Security Policy
Today, as part of our quarterly threat reporting, we’re sharing a number of security updates, including our Q1 Adversarial Threat Report and insights into our work against malware campaigns.
Over the past five years, we’ve shared our findings about threats we detect and remove across our technologies. In this threat report, we’re sharing information about six networks we took down for violating our policies against coordinated inauthentic behavior (CIB) and three cyber espionage operations we took action against. We have shared information about our findings with industry partners, researchers and policymakers. Here are the key insights from our first quarter 2023 Adversarial Threat Report:
We took action against three cyber espionage operations in South Asia. One was linked to a group of hackers known in the security industry as Bahamut APT (advanced persistent threat), one to the group known as Patchwork APT, and another to the state-linked actors in Pakistan. Here is what stood out from our threat research:
We also took down six covert influence operations for violating our policy against CIB. These unconnected networks originated in the United States, Venezuela, Iran, China, Georgia, Burkina Faso and Togo. More than half of them targeted audiences outside of their countries. We removed the majority of these operations before they were able to build authentic audiences. Here is what stood out from our threat research:
We know that adversarial threats will keep evolving in response to our enforcement and that new malicious behaviors will emerge. We’ll continue to refine our enforcement and share our findings publicly.
We are making progress in rooting out this abuse; it is an ongoing effort and we’re committed to continually improving to stay ahead. On May 12, the Irish Data Protection Commission (IDPC) plans to issue a decision on whether to stop Meta from transferring personal data to the United States. The IDPC is Meta’s lead European Union privacy regulator under the General Data Protection Regulation (GDPR), Meta’s 10-Q for Q1 2023 stated.
Meta discussed the upcoming EU ruling in its April 26 earnings call, in which it announced first quarter 2023 revenue hit nearly $28.7 billion, an increase of 3% year over year. The company said it’s consulting with policymakers who expect a new EU-US Data Privacy Framework before a data transfer suspension would occur. However, Meta is preparing in case this agreement comes after the deadline.
Meta doesn’t expect to be forced to comply with the data transfer ruling before the fourth quarter of 2023, according to the 10-Q filing. (7)
See the full Adversarial Threat Report for more information.
During an earnings call, Meta revealed that an Irish Data Protection Commission decision on data transfers could impact 10% of its ad revenue
Waiting for a transatlantic regulatory agreement might force Meta to halt Facebook and other European services. On May 12, the Irish Data Protection Commission (IDPC) plans to issue a decision on whether to stop Meta from transferring personal data to the United States. The IDPC is Meta’s lead European Union privacy regulator under the General Data Protection Regulation (GDPR), Meta’s 10-Q for Q1 2023 stated. Meta discussed the upcoming EU ruling in its April 26 earnings call, in which it announced first quarter 2023 revenue hit nearly $28.7 billion, an increase of 3% year over year. The company said it’s consulting with policymakers who expect a new EU-US Data Privacy Framework before a data transfer suspension would occur. However, Meta is preparing in case this agreement comes after the deadline.
Meta doesn’t expect to be forced to comply with the data transfer ruling before the fourth quarter of 2023, according to the 10-Q filing. About 10% of Meta’s worldwide ad revenue originates from ads delivered to Facebook users in EU countries. The impact on advertisers due to a data transfer suspension is unknown, according to Meta CFO Susan Li. She said the company is hopeful a new EU-US privacy framework will be completed before a suspension occurs. “But if it comes to that, there’s a lot that we don’t know in terms of the specifics of a final order and how long a suspension order would last, which would be important variables in determining the overall impact,” Li said. (12)
…the Commission notes that the breadth and significance of these deficiencies pose substantial risks to the public
The Federal Trade Commission alleges that Meta has “repeatedly violated” privacy rules and proposes to tighten the agency’s 2020 order against the company, completely barring it from monetizing data from anyone under 18 in any way, among other new restrictions. The order in question took effect in 2020 but was created in 2019 as part of then-Facebook’s $5 billion settlement after the company violated a previous order. Now the FTC says that Facebook/Meta has violated the new order, as well as the Children’s Online Privacy Protection Act Rule. “The company’s recklessness has put young users at risk, and Facebook needs to answer for its failures,” said Samuel Levine, director of the FTC’s Bureau of Consumer Protection, in a news release. (Due to the order and said failures spanning both names of the company, both are also used throughout.)
The 2020 order created an independent third-party assessor who would evaluate whether Meta was adhering to the privacy rules, things like having new products go through privacy reviews and restrictions on how facial recognition data and phone numbers are used. This assessor recently gave the FTC their report, and apparently, it is not pretty, containing evidence of numerous shortcomings or violations: “the Commission notes that the breadth and significance of these deficiencies pose substantial risks to the public,” the agency wrote. Specifically, Facebook promised (in 2018 — the timeline is long and confusing) to cut off app developers’ access to users’ data if that user had not used the app in 90 days. But it did not do so, the FTC alleges and allowed some of that data to be used well into 2020. (9)
“Different investigators can get together and say, ‘Hey, are we seeing the same thing?”
Next year will feature some of the most geopolitically significant elections of our times. Voters will be heading to the ballot boxes in not only the United Kingdom, United States and European Union, but also India, Turkey and Taiwan.
Anticipating an even greater need for “investigative teams across industry, civil society, and government” to collaborate against online interference in these elections, Meta published on…a new Online Operations Kill Chain framework for analyzing and responding to these threats.
The framework is a tool used internally at Meta to formally “analyze individual operations and identify the earliest moments at which they can be detected and disrupted.” The parent company of Facebook and Instagram hopes it will help other defenders detect and disrupt operations when they see them on their networks, too, and help everybody share their findings. (10)
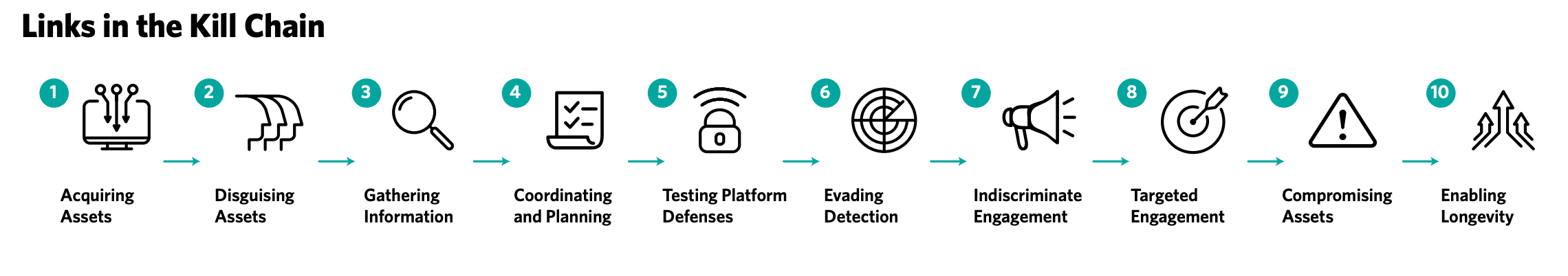 Image Source: The Record
Image Source: The Record
The Record spoke about the new model to two of the company’s leading security experts, Ben Nimmo, Meta’s global threat intelligence lead, and Eric Hutchins, a Security Engineer Investigator on the influence operations team. Nimmo previously helped expose foreign election interference in the United States, United Kingdom, and France. Hutchins, who previously worked at Lockheed Martin, invented the Intrusions Kill Chain model based on the military concept of a “kill chain,” which formally describes the separate phases of an attack, from identifying a target through to its destruction.
Nimmo and Hutchins introduced the model at CYBERWARCON back in November: Breaking the silos — CYBERWARCON
The Record interview with Nimmo and Hutchins can be found here.
…Meta says it disrupted a novel malware family within weeks after it emerged earlier this year.
Dubbed NodeStealer, the threat was designed to steal cookies and usernames, and passwords from browsers such as Chrome, Edge, Brave, and Opera, to compromise online accounts. A custom JavaScript malware first observed in January 2023, NodeStealer is likely of Vietnamese origin, being distributed disguised as PDF and XLSX files. This week, Meta revealed that it first identified NodeStealer roughly two weeks after it was first deployed and that it immediately took action to neutralize it, including by contacting appropriate services providers. “As part of this effort, we submitted takedown requests to third-party registrars, hosting providers, and application services such as Namecheap, which were targeted by these threat actors to facilitate distribution and malicious operations,” Meta explains.
According to the tech giant, the disruption was successful, as no new NodeStealer samples have been observed since February 27. NodeStealer is executed using the cross-platform, open-source JavaScript runtime environment Node.js, Meta explains. The threat uses the auto-launch module of Node.js to achieve persistence, adding a new registry key to ensure it runs at startup.
On infected machines, the malware harvests encrypted browser data that it then decrypts to retrieve the cookie database and stored credentials. “The malware specifically targets user credentials for Facebook, Gmail, and Outlook. We hypothesize that the malware steals email credentials to compromise the user’s contact point and potentially to access other online accounts connected to that email account,” Meta says.
NodeStealer was also observed making unauthorized requests to Facebook URLs to retrieve account details related to advertising. The threat actor behind the malware then leverages this information to run unauthorized ads using the victims’ advertising accounts. The malware sends all harvested information to its command-and-control (C&C) server, in a Base64-encoded JSON object. The C&C domain was registered on December 27, 2022 and was suspended on January 25, 2023. (11)
https://oodaloop.com/archive/2023/04/21/the-current-on-chip-innovation-and-physical-layer-market-dynamics-of-gpt-model-training-crypto-mining-and-the-metaverse/
“Meta and Qualcomm are teaming up to develop custom chipsets for virtual reality products, the companies announced on Friday.
The two U.S. technology giants have signed a multi-year agreement “to collaborate on a new era of spatial computing,” using Qualcomm’s “extended reality” (XR) Snapdragon technology. Extended reality refers to technologies including virtual and augmented reality, which merge the physical and digital world.
The Quest products are Meta’s line of virtual reality headsets. The Meta Quest 2 headset currently uses Qualcomm’s Snapdragon XR2 chipset.
Since its rebrand in 2021, Facebook-parent Meta has staked its future on the metaverse — a term that encompasses virtual and augmented reality technology — with the aim of having people working and playing in digital worlds in the near future.
In the smartphone field, companies ranging from Apple to Samsung have designed their own custom processors to differentiate from competitors and create better products than they might have using off-the-shelf chips.
A focus on custom chips by Meta makes sense as it looks to differentiate its headsets and possibly create unique experiences for users.
“Unlike mobile phones, building virtual reality brings novel, multi-dimensional challenges in spatial computing, cost, and form factor,” Zuckerberg said. “These chipsets will help us keep pushing virtual reality to its limits and deliver awesome experiences.”
The length of the deal between the companies and the financial terms of the deal were not disclosed.
It comes as Meta gears up to launch a new virtual reality headset in October, even as losses widened in its Reality Labs division, which includes its VR business, in the second quarter of the year.” (14)
For a more detailed report of this development, see Meta Partners With Qualcomm To Develop Customized Chips for the Metaverse.
https://oodaloop.com/archive/2023/04/19/did-airman-teixeira-give-you-concern-just-wait-for-the-metaverse/
https://oodaloop.com/archive/2023/05/09/ai-enabled-image-generation-midjourney-dall-e-stable-diffusion/
https://oodaloop.com/archive/2023/03/31/a-discussion-of-exponential-growth-and-the-metaverse-with-qwerx-coo-and-ooda-network-member-randall-fort/