Start your day with intelligence. Get The OODA Daily Pulse.
Start your day with intelligence. Get The OODA Daily Pulse.
According to a new FBI report, there has been a shocking rise in the so-called “Tech Support” scam, in which the fraudster poses as a technical or customer support representative. There are many types of scams, but the Tech Support scam is in a league all its own. This scam has shown particularly eye-popping growth in recent years, and it is hitting the nation’s elderly particularly hard. The Tech Support scam has been around for over 10 years. Despite significant public education over the years, the problem is getting much, much worse. Unless urgent steps are taken, the losses will mount as the population ages and as artificial intelligence increasingly offers fraudsters even more credible ways to be convincing.
No one likes to think scammers could defraud their family or friends, but believe me, they can. Maybe they already have. Most readers of this article probably know someone who has been victimized by internet-based fraud in recent years. Keep in mind that crimes such as this are not only financial; the victims suffer significant emotional distress as well, for the rest of their lives. More broadly, “Malicious cyber activity threatens the public’s safety and our national and economic security,” according to the FBI. Law enforcement officials have found that organized crime gangs are shifting to consumer fraud to finance their crimes because it’s so easy to do.
What can we do as a society to help protect seniors from further victimization? The problems are complex and multifaceted. Today, consumers cannot easily discern honest behavior in their Internet activity from dishonest behavior. They can’t tell a malicious link from a good one. They can’t tell whether they are communicating with a trusted company or a hacker. Therefore, we need to provide trusted and authenticated communications via the Internet, phone, and text. Other solutions involve the software industry, banks, law enforcement, and public education. One thing is clear: technology providers need to step up to take on more of the burden of fraud prevention. Individuals can’t do it on their own.
[Note: we are actively soliciting new ideas for new approaches here, contact us by reply to any of our newsletters or via our inquiry page if you can contribute to the dialog]

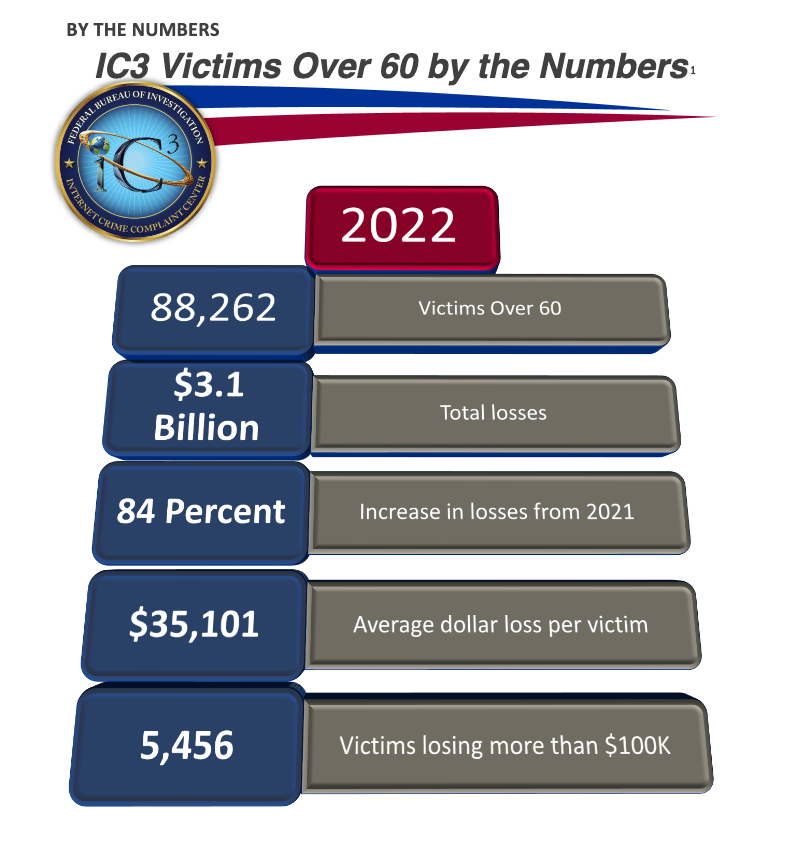
In late April 2023, the FBI’s Internet Crime Complaint Center (IC3) released a summary of the reports of fraud it received in 2022. The report found that in 2022, overall losses reported by elderly victims increased 84% from 2021. But losses from Tech Support scams shot up 147% over that same period. Reported losses from Tech Support scams have skyrocketed over 400% since 2020. Tech and Customer Support schemes continued to be the most common type of fraud reported, with 17,800 complaints filed by victims over 60. The Tech Support fraud accounts for the largest number of victims and the second-highest amount of losses reported (after the “investment” scams). Nearly $588 million in losses for the Tech Support scam were reported in 2022–that’s over $33,000 per victim. The reported losses from Tech Support victims amounted to nearly 10 times the amount of losses reported due to credit card/check fraud.

According to the 2022 FBI report, victims over 60 lost more to “Call Center” scams (including Tech Support) than all other age groups combined. Seniors reportedly remortgaged/foreclosed homes, emptied retirement accounts, and borrowed from family and friends to cover losses in these scams. Almost 100 elderly victims reportedly lost over $1 million. The number of victims of this type of fraud has more than doubled in the last four years, and losses have skyrocketed.

The FBI says this type of scam primarily emanates from call centers in South Asia, mainly India. The Department of Justice and the FBI work with law enforcement in India, and Indian police have arrested individuals alleged to be involved in cyber-enabled crimes. But the rapid growth in these frauds indicates that law enforcement is not stemming the rapidly rising tide of fraud.
Why are Tech Support scams able to succeed, and what can be done to stop them?

Pop-up ads from scammers can take a variety of forms
There are many factors that contribute to the scammers’ ability to succeed.
Pop-up ads (windows that appear without your permission) often serve as the entry point for the perpetrators of the Tech Support scam. It is too easy for scammers to place a pop-up ad on a person’s computer that cannot be closed, and therefore appears to “take over” the person’s computer. In the case of one person I know, an audio message also blared a warning: “DO NOT TURN OFF YOUR COMPUTER.” Pop-ups can be delivered many different ways, including malicious advertisements, phishing emails, and malicious websites. To make matters worse, malvertising is not stopped by traditional security tools like anti-virus software. Companies like Facebook and Google try to block or remove the ads, but a more aggressive approach is clearly needed.
Remote access tools (RATs). Fraudsters typically use social engineering techniques to coax victims into installing software that allows the criminals to control the victim’s computer. Some common RATs include Ammy, AnyDesk, Citrix, Chrome Remote Desktop, Fastsupport, LogMein, ShowMyPC, Supremo, TeamViewer, UltraViewer, and Go2Assist. Once installed, these tools can run for months or even years without warning the victims that someone else is viewing and controlling their computer. And anti-virus software does not warn the victims because RATs are treated as “known good” software.
Telephone/text anonymity. Scammers often pose as calling from US companies like Microsoft or Apple, and victims cannot see that the call is actually originating in South Asia, from a number that doesn’t belong to Microsoft or Apple. Bad actors also regularly impersonate banks, credit unions, healthcare companies, and other legitimate callers by illegally ‘spoofing’ phone numbers belonging to these businesses. The FCC has made much progress in recent years to ensure that Caller ID authentication, based on “STIR/SHAKEN” standards, provides a common information-sharing language between networks. The new standards can verify caller ID information, which can be used by robocall blocking tools, FCC investigators, and consumers trying to judge if an incoming call is likely legitimate or not. Meanwhile, the UK government is taking action to reduce phone number spoofing. The British Prime Minister recently announced an initiative to work with UK’s communications regulator to prevent scammers from impersonating UK numbers and tricking people into thinking they’re speaking to banks, telephone companies or other legitimate businesses.
Insufficient public education. Many news stories appeared about the Tech Support scam in the 2010s, but press coverage of this issue has dropped off in recent years. Meanwhile, Medicare, the Federal Trade Commission, and AARP recently joined forces to create Public Service Announcements to alert seniors to the threat of Medicare fraud (in English and Spanish). But there has not been a similar nationwide effort with regard to internet-based frauds, including the Tech Support fraud.
Banking education and accountability. Fraudsters often convince seniors to transfer funds via cashier’s checks or wire transfers.
An urgent nationwide effort is needed. On 3 May the British Prime Minister announced a comprehensive strategy with over 50 actions to combat fraud in the UK, saying “Fraud now accounts for over 40% of crime. It costs us nearly £7 billion ($8.72 billion) a year and we know these proceeds are funding organised crime and terror.”
Similar action is needed in this country, and our guiding principle should be the March 2023 National Cybersecurity Strategy, which calls for the burden of security to be shifted from individuals to the technology providers. The Strategy says: “The most capable and best-positioned actors in cyberspace must be better stewards of the digital ecosystem. Today, end users bear too great a burden for mitigating cyber risks. Individuals, small businesses, state and local governments, and infrastructure operators have limited resources and competing priorities, yet these actors’ choices can have a significant impact on our national cybersecurity. A single person’s momentary lapse in judgment, use of an outdated password, or errant click on a suspicious link should not have national security consequences. Our collective cyber resilience cannot rely on the constant vigilance of our smallest organizations and individual citizens.
Instead, across both the public and private sectors, we must ask more of the most capable and best-positioned actors to make our digital ecosystem secure and resilient. In a free and interconnected society, protecting data and assuring the reliability of critical systems must be the responsibility of the owners and operators of the systems that hold our data and make our society function, as well as of the technology providers that build and service these systems.”
It is high time we started down that path. After all, we will all be seniors someday, and seniors can’t successfully fight the fraudsters alone.