In response to the Tweet string above, OODA CEO Matt Devost added (via his Global Frequency weekly blast): “L3 looks to buy NSO Group. We should not allow a company like NSO, which has sold offensive cyber capabilities to regimes using them in non-humanitarian ways and against U.S. interests and is also under current sanctions to profit from this activity. There are plenty of U.S. entities that can provide these capabilities without the baggage.” For more context on the NSO Group, see our recent update – The NSO Group’s Pegasus Spyware: A Global Update.
In the shadow of this discouraging market activity, we return to a research report released by The Atlantic Council in November of last year entitled “Surveillance Technology at the Fair: Proliferation of Cyber Capabilities in International Arms Markets” as part of their Cyber Statecraft Initiative. In the report, the Council researchers place the availability of cyber capabilities in the context of the mature marketplace represented by annual international arms markets (which is a really creative framework for research on the growth of cyber-surveillance capabilities in the private sector).
The researchers do an analysis of the cyber-surveillance technology market as an adjacent market – and discern growth metrics, scope of the size of the market, etc. Following is an analysis of the major findings of the report. The MIT Technology Review in their coverage of the report captured the overall sentiment of the researchers this way: “The increasing overlap between the world’s arms trade and the secretive surveillance industry risks damaging US national security and will create the potential for even more abuse unless more accountability is introduced, according to a new study.” (1)
Surveillance Technology at the Fair: Proliferation of Cyber Capabilities in International Arms Markets
Methodology, Assumptions, and Limitations
- “The research…offers one of the most thorough accountings ever assembled of a booming, cross-continental surveillance industry that makes billions of dollars and yet mostly manages to stay out of the limelight.”
- “The report is based on 20 years of data collected from the cyber-surveillance trade show ISS World and arms fairs like France’s Milipol, where hacking is the fastest-growing business segment alongside more traditional wares like guns and tanks.”
- “Its authors examined 224 surveillance companies present at these shows, looked at their marketing material, examined where in the world they advertised their products and detailed the known sales of surveillance and hacking tools.” (1)
Introduction
From the Executive Summary of the report: “State cyber capabilities are increasingly abiding by the “pay-to-play” model—both US/NATO allies and adversaries can purchase interception and intrusion technologies from private firms for intelligence and surveillance purposes. NSO Group has repeatedly made headlines in 2021 for targeting government entities in cyberspace, but there are many more companies selling similar products that are just as detrimental. These vendors are increasingly looking to foreign governments to hawk their wares, and policymakers have yet to sufficiently recognize or respond to this emerging problem. Any cyber capabilities sold to foreign governments carry a risk: these capabilities could be used against individuals and organizations in allied countries, or even in one’s home country.”
This paper profiles these important trends for their practical security impacts, and to enable further research into this topic. The authors suggest that the United States and NATO:
- Create know-your-customer (KYC) policies with companies operating in this space;
- work with arms fairs to limit irresponsible proliferators’ attendance at these events;
- tighten export-control loopholes; and
- name and shame both irresponsible vendors and customers.
The authors encourage policymakers to focus their efforts to rein in companies that sell these capabilities directly to adversaries, or those willing to ignore the risk that their capabilities may be misused. The dataset presented below is open for use by others who might similarly seek to bring some measure of light to an industry that remains so insistently in the dark.” (3)
Main Findings (4)
Of the research reports we have used for research and provided to the OODA Loop membership, this report’s online version has a brilliant interactive visualization format packed full of quantitative findings. Each of the links below will take you to these four main findings sections of the report:

- What firms are marketing their interception/intrusion capabilities at arms fairs?: Of the two hundred and twenty-four organizations total (full list in the Appendix), fifty-nine are high-confidence matches. The authors assess these companies are highly likely to market interception/intrusion technologies at any arms fair they attend. Some of the companies (like Croatia’s Pro4Sec and India’s ClearTrail) advertise lawful interception services on their websites for military, law enforcement, and intelligence agency clients. Others (like Italy’s Area s.p.a and Germany’s Wolf Intelligence) have vague websites or no websites at all but have been called out by news media for selling interception/intrusion tools. (25) (26)
- What companies are marketing interception/intrusion capabilities outside their headquartered region?: This question focuses only on the high/medium-confidence companies, as the authors cannot assess whether the low-confidence companies have been marketing these capabilities at arms fairs with enough certainty. For the high/medium-confidence companies, the data show a general willingness to market interception/intrusion capabilities internationally, even to foreign countries that do not have established intelligence relationships or alliances with the company’s home country. Almost 75 percent of the eighty-one high/medium-confidence companies have exhibited their wares to arms fairs outside of their home continent in the last twenty years. More than 85 percent have exhibited at arms fairs outside their home country in the last twenty years. This excludes the two firms headquartered in Five Eyes countries that have only been to arms fairs in a Five Eyes country. (The full list of the sixty firms is in the Appendix.) When broken down by year, this trend remains consistent; of all the firms marketing to arms fairs in a given year, more firms market to arms fairs outside their continent in a given year than restrict sales to their continent or country.
- Which arms fairs (and arms fair host countries) host the most high/medium-confidence firms?: While the two hundred and twenty-four companies in the dataset hail from thirty-three separate countries, most of the companies congregate at a small number of arms fairs, many of which are located in Europe. Milipol France and Security & Policing Home Office (based in the UK) are the two most widely attended arms fairs for the high/medium-confidence firms selling interception/intrusion capabilities. This is likely due to size and specialization, respectively. Milipol France is one of the world’s largest arms fairs, with more than one thousand exhibitors, while Security & Policing has a track dedicated to cybersecurity. (30)
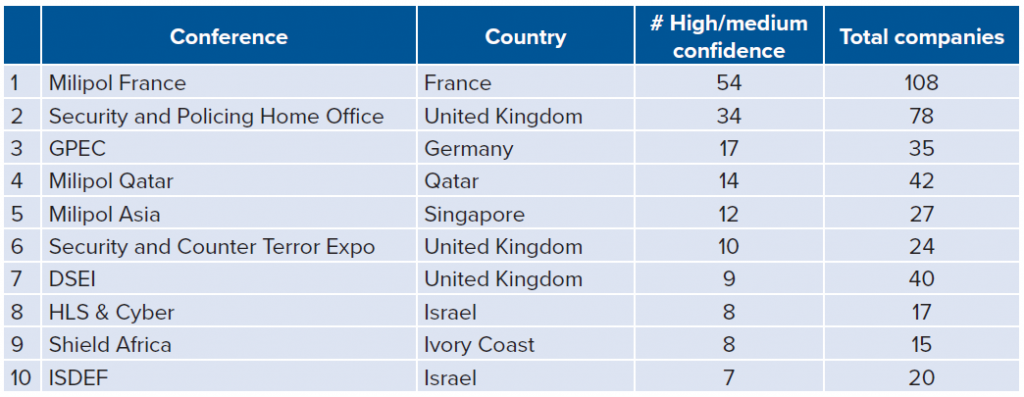
France and the UK are also the top countries where high/medium-confidence firms congregate, mostly due to the two aforementioned conferences. Germany, Singapore, Qatar, and Israel are also common destinations for high/medium-confidence firms, while the United Arab Emirates and the United States play host to more firms overall, thanks to a variety of smaller arms fairs.
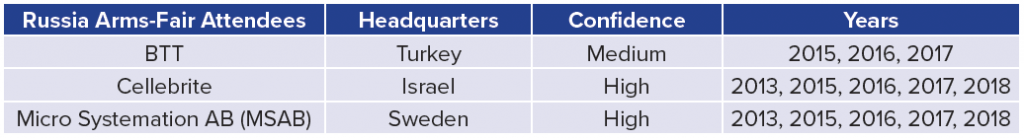
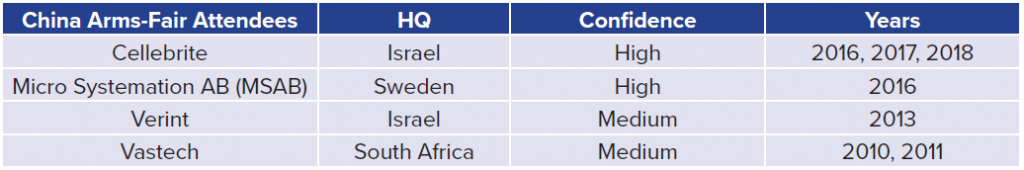
- What companies are marketing interception/intrusion capabilities to US and NATO adversaries?: Five of the eighty-one high/medium-confidence firms have attended arms fairs in Russia and China as exhibitors in the last twenty years. This excludes any firms also headquartered in Russia and China. For example, Norsi Trans is a high-confidence Russian company that has attended Russian arms fairs in 2009, 2010, 2015, 2016, 2017, 2018, and 2019. The authors believe that by selling to these parties, these organizations are willing to accept or ignore the risk that their products may bolster the capabilities of adversary governments, who may use their products to conduct espionage more effectively. For example, Cellebrite, a well-known Israeli firm, has consistently been an exhibitor at arms fairs in both China and Russia from 2013 onward and is the only firm in the dataset to attend a Chinese arms fair multiple times in the last five years. Cellebrite, which sells software to physically extract and index data from mobile devices, is known to have both Chinese and Russian customers. (31)Some of the other firms in the below tables have received less media attention than Cellebrite, but are no less concerning. BTT is a Turkish firm that has assisted Turkish law enforcement with a call-detail record collection. (32) In a 2017 Al Jazeera investigation of the spyware market, BTT representatives claimed to use a wide interpretation of “telecommunications equipment” in order to circumvent export-control paperwork. (33) MSAB, a firm that has also marketed to both Russia and China, sells mobile forensics products that have been used against activists in Hong Kong and Myanmar. (34)
Conclusions and Recommendations
- “After years of rising demand for hacker-for-hire products and an increase in reported abuses by companies like NSO Group, countries around the world are now trying to deal with this largely hidden industry.”
- The Atlantic Council researchers ” also argue that numerous companies that market internationally, especially to adversaries of NATO, are “irresponsible proliferators” and deserve more attention from policymakers.” (1) As the report says: “When these firms begin to sell their wares to both NATO members and adversaries, it should provoke national security concerns by all customers.” (2)
- Irresponsible Proliferators include “Israel’s Cellebrite, which develops phone hacking and forensics tools, and which sells around the world to countries including the US, Russia, and China. The company has already faced significant blowback because of, for example, its role during China’s crackdown in Hong Kong and the discovery that its technology was being used by a Bangladeshi ‘death squad.‘
- “The trade is increasingly global, according to the report, with 75% of companies selling cyber-surveillance and intrusion products outside their own home continent. Lead author Winnona DeSombre, a fellow with the Atlantic Council’s Cyber Statecraft Initiative, argues that such sales signal potential problems with oversight. ‘There does not seem to be a willingness to self-regulate for a majority of these firms,’ she says. By marking such firms as ‘irresponsible proliferators,’ DeSombre hopes to encourage lawmakers around the world to target some companies for greater regulation.” (1)
- One obstacle is that the cyber-surveillance industry is rife with obfuscation: shell companies and resellers are common, and both sellers and buyers use a host of tools to hide their interactions. ‘There is not enough knowledge about the industry in the public, where you can delineate the irresponsible firms from the responsible,’ says DeSombre.
- ‘The most basic takeaway from this paper is that we are dealing with an industry,’ says Johann Ole Willers, a fellow at the Norwegian Institute of International Affairs (NUPI) Centre for Cyber Security Studies. ‘That is a fundamental insight. It’s not enough to target NSO Group.’ (1)
A PDF of the report can be found here.
What Next?
Stay Informed
It should go without saying that tracking threats are critical to informing your actions. This includes reading our OODA Daily Pulse, which will give you insights into the nature of the threat and risks to business operations.
Related Reading:
Explore OODA Research and Analysis
Use OODA Loop to improve your decision-making in any competitive endeavor. Explore OODA Loop
Decision Intelligence
The greatest determinant of your success will be the quality of your decisions. We examine frameworks for understanding and reducing risk while enabling opportunities. Topics include Black Swans, Gray Rhinos, Foresight, Strategy, Stratigames, Business Intelligence, and Intelligent Enterprises. Leadership in the modern age is also a key topic in this domain. Explore Decision Intelligence
Disruptive/Exponential Technology
We track the rapidly changing world of technology with a focus on what leaders need to know to improve decision-making. The future of tech is being created now and we provide insights that enable optimized action based on the future of tech. We provide deep insights into Artificial Intelligence, Machine Learning, Cloud Computing, Quantum Computing, Security Technology, Space Technology. Explore Disruptive/Exponential Tech
Security and Resiliency
Security and resiliency topics include geopolitical and cyber risk, cyber conflict, cyber diplomacy, cybersecurity, nation-state conflict, non-nation state conflict, global health, international crime, supply chain, and terrorism. Explore Security and Resiliency
Community
The OODA community includes a broad group of decision-makers, analysts, entrepreneurs, government leaders, and tech creators. Interact with and learn from your peers via online monthly meetings, OODA Salons, the OODAcast, in-person conferences, and an online forum. For the most sensitive discussions interact with executive leaders via a closed Wickr channel. The community also has access to a member only video library. Explore The OODA Community
About the Author
Daniel Pereira
Daniel Pereira is research director at OODA. He is a foresight strategist, creative technologist, and an information communication technology (ICT) and digital media researcher with 20+ years of experience directing public/private partnerships and strategic innovation initiatives.
Subscribe to OODA Daily Pulse
The OODA Daily Pulse Report provides a detailed summary of the top cybersecurity, technology, and global risk stories of the day.



