Last week, a new hacking group took responsibility for the taking down of a Russian telecom satellite, which we interpreted as an expansion of the tactical activity (brought on by the instability in Russia) by Advanced Persistent Threats (APTs) and non-state cyber actors on all sides of the multi-sided hybrid conflict in Europe. The following cyber incidents in the last week are consistent with a pattern of an increase in cyber attacks related to the Ukrainian conflict.
Russian railway site was allegedly taken down by Ukrainian hackers (July 5, 2023)
“Cyberattacks targeting railways…hinder the transfer of Russian troops into Belarus for military exercises.”
- The Russian state-owned railway company RZD said Wednesday that its website and mobile app were down for several hours due to a “massive” cyberattack, forcing passengers to only buy tickets at railway stations.
- The Ukrainian hacktivist group IT Army claimed responsibility for the attack on its Telegram channel. “The terrorist state is heading non-stop to the station called Chaos,” the hackers said. The group’s claims could not be immediately verified.
- RZD’s system was down for at least six hours, but the company said later on Wednesday that it had restored its operation despite ongoing attacks. Some of the company’s online services are still unavailable due to the increased load, RZD said.
- “Our goal is not to permanently take down the website. It requires significant effort to prepare an attack on such a target,” said IT Army. “Even if the website is down only for an hour, it would still have a significant impact on the economy of the aggressor country.”
- It is the second attack on RZD since the start of the war in Ukraine. Last February, the Russian railway’s website and mobile app were also down due to intense distributed denial-of-service (DDoS) attacks. Such attacks work by flooding a targeted site with junk traffic, making them unreachable.
- At the time of the incident, the company increased the number of ticket offices at railway stations so that all passengers could buy tickets.
- Cyberattacks targeting railways can greatly disrupt a country’s logistics. Last year, a cyberattack on the Belarusian state railway crippled its network, allegedly hindering the transfer of Russian troops into Belarus for military exercises. The Belarusian hacktivist collective Cyber Partisans, which claimed responsibility for the attack, said that some trains stopped running after hackers compromised the railway system’s routing and switching devices and rendered them inoperable by encrypting data stored on them. (1)
Belarusian hacktivists сlaim to breach the country’s leading state university (July 5, 2023)
“…are you sure you want to play this game with us? You’d better beg the dictator to release political prisoners.”
- The Belarusian hacker group known as the Cyber Partisans is claiming an attack on the country’s largest state-owned university. The Belarusian State University (BSU) is located in the capital city of Minsk and has over 44,800 students.
- The Cyber Partisans said they have been trying to access its systems for over two months and finally succeeded this week.
- “It took us time to infiltrate the network and gain a foothold there,” the hackers said. “Our goal was to cause maximum damage so that BSU could not recover for a long time.”
- The Cyber Partisans claimed to have accessed 3 terabytes of data from the university’s system. They claim to have encrypted and wiped computers and servers, and also shut down the domain controllers responsible for managing user authentication and network security.
- At this story’s time of publication on Wednesday [July 5, 2023], the Belarusian State University website is still down.
- The university denied any cyberattack and attributed the system’s downtime to technical issues. Officials also claimed that the photos and screenshots shared by the hackers were fake and photoshopped.
- Belarusian hacktivists, known for their politically motivated attacks on the regime of Belarusian dictator Alexander Lukashenko and as well as Russian targets, said they would exchange stolen data for the release of 50 prisoners detained for opposing the government.
- Since 2020, when massive anti-government protests began in Belarus following a controversial presidential election believed to have been rigged by Lukashenko, BSU students have been intimidated and expelled because of their political views, according to the Cyber Partisans.
- In April, BSU posted a video of a student who was forced to apologize on camera for allegedly “discrediting” the university. “When you act as oppressors, you make yourselves a target for our cyberattacks,” the Cyber Partisans said.
- The hackers said they had not planned to attack the university but were appalled by the video. “It was filmed in an institution that should educate, not promote violence,” they said.
- The Cyber Partisans said they managed to get into the system by obtaining the password of one of a student who has higher-level access. Then they accessed BSU’s email and cloud services, as well as its website, ultimately infiltrating the servers and internal network.
- After BSU issued its statement denying the attack, the Cyber Partisans retaliated by sharing additional screenshots from the university president’s email, including excerpts from his bank account.
- “We have over 3 terabytes of data from your servers—are you sure you want to play this game with us? You’d better beg the dictator to release political prisoners,” the hackers said. (2)
https://oodaloop.com/cyber/2023/07/05/ddosia-attack-tool-evolves-with-encryption-targeting-multiple-sectors/
Pro-Russian hackers upgrade DDoSia bot used to attack Ukraine, NATO countries
“Sekoia only observed one incident when the group attacked a single victim — Russia’s Wagner private mercenary army during its attempted military coup in June.”
- The DDoSia project by pro-Russian hackers has seen significant growth this year as attackers continue to use the technology against countries critical of Russia’s invasion of Ukraine.
- DDoSia is a distributed denial-of-service attack toolkit developed and used by the pro-Russia hacktivist group NoName057(16).
- The group and its followers are actively deploying the tool against government agencies, media, and private companies in Lithuania, Ukraine, Poland, Italy, and other European countries, according to a report released by cybersecurity company Sekoia this week.
- “This likely stems from the fact that those countries are the most vocal in public declarations against Russia and pro-Ukraine, as well as providing military support and capabilities,” the researchers said.
- Sekoia detected a total of 486 different websites impacted by DDoSia attacks. Among them are incidents involving Latvia’s parliament and Poland’s tax service.
- NoName057(16) also targeted education-related websites during the exam period in Ukraine in May and June, allegedly to maximize the media coverage of their DDoS operation, Sekoia said.
- The group typically targets 15 different victims per day. Sekoia only observed one incident when the group attacked a single victim — Russia’s Wagner private mercenary army during its attempted military coup in June. DDoS attacks are designed to overwhelm network resources with traffic to effectively take them offline. (3)
Technical Details
“DDoSia is distributed through a fully-automated process on Telegram that allows…for…crowdsourcing…in exchange for a cryptocurrency payment and a ZIP archive containing the attack toolit.”
- The updated variant, written in Golang, “implements an additional security mechanism to conceal the list of targets, which is transmitted from the [command-and-control] to the users,” cybersecurity company Sekoia said in a technical write-up.
- DDoSia is attributed to a pro-Russian hacker group called NoName(057)16. Launched in 2022 and a successor of the Bobik botnet, the attack tool is designed for staging distributed denial-of-service (DDoS) attacks against targets primarily located in Europe as well as Australia, Canada, and Japan.
- Python and Go-based implementations of DDoSia have been unearthed to date, making it a cross-platform program capable of being used across Windows, Linux, and macOS systems.
- “DDoSia is a multi-threaded application that conducts denial-of-service attacks against target sites by repeatedly issuing network requests,” SentinelOne explained in an analysis published in January 2023. “DDoSia issues requests as instructed by a configuration file that the malware receives from a C2 server when started.”
- DDoSia is distributed through a fully-automated process on Telegram that allows individuals to register for the crowdsourced initiative in exchange for a cryptocurrency payment and a ZIP archive containing the attack toolkit.
- What’s noteworthy about the new version is the use of encryption to mask the list of targets to be attacked, indicating that the tool is being actively maintained by the operators.
- “NoName057(16) is making efforts to make their malware compatible with multiple operating systems, almost certainly reflecting their intent to make their malware available to a large number of users, resulting in the targeting of a broader set of victims,” Sekoia said. (4)
 Source: Sekoia
Source: Sekoia
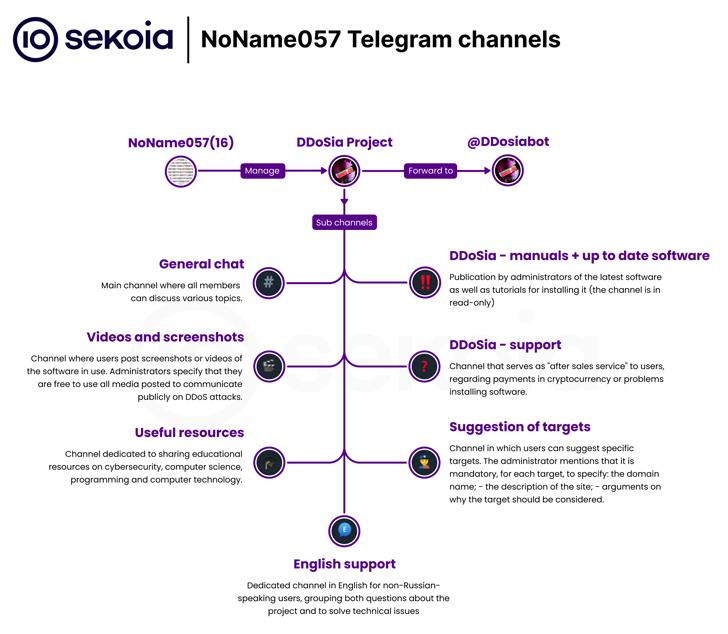
Telegram communications
“It is highly likely we will observe further developments in the short term…”
- The DDoSia project was launched in early 2022, reaching 10,000 followers on its Telegram channel. The administrators of the group, as well as community members, are very active, according to Sekoia. The group regularly posts messages about successful attacks.
- NoName057(16) also communicates about the project through its own Telegram channels, including one in Russian with over 45,000 subscribers, and a separate channel in English.
- Volunteers who choose to participate in hacking campaigns are paid in cryptocurrency based on their contribution to DDoS attacks. Before launching the attack, the new members receive a .zip archive that contains the attack toolkit.
- According to Sekoia, the NoName057(16) group continues to update the DDoSia project. For example, they want to make their malware compatible with multiple operating systems to reach more targets.
- “It is highly likely we will observe further developments in the short term,” the researchers said. (3)
What Next? Increased DoS and DDoS Attacks
“CISA’s latest advisory has also not gone unnoticed…”
- The development comes as the U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned of targeted denial-of-service (DoS) and DDoS attacks against multiple organizations in multiple sectors.
- “These attacks can cost an organization time and money and may impose reputational costs while resources and services are inaccessible,” the agency said in a bulletin.
- Although CISA did not provide any additional specifics, the warning overlaps with claims by Anonymous Sudan on its Telegram channel that it had taken down the websites of the Department of Commerce, Social Security Administration (SSA), and the Treasury Department’s Electronic Federal Tax Payment System (EFTPS).
- Anonymous Sudan attracted attention last month for carrying Layer 7 DDoS attacks against various Microsoft services, including OneDrive, Outlook, and Azure web portals.
- The tech giant is tracking the cluster under the name Storm-1359.
- The hacking crew has asserted it’s conducting cyber strikes out of Africa on behalf of oppressed Muslims across the world. But cybersecurity researchers believe it to be a pro-Kremlin operation with no ties to Sudan and a member of the KillNet hacktivist collective.
- In an analysis released on June 19, 2023, Australian cybersecurity vendor CyberCX characterized the entity as a “smokescreen for Russian interests.” The company’s website has since become inaccessible, greeting visitors with a “403 Forbidden” message. The threat actor claimed responsibility for the cyber attack.
- “The reason for the attack: stop spreading rumors about us, and you must tell the truth and stop the investigations that we call the investigations of a dog,” Anonymous Sudan said in a message posted on June 22, 2023. Anonymous Sudan, in a Bloomberg report last week, further denied it was connected to Russia but acknowledged they share similar interests, and that it goes after “everything that is hostile to Islam.”
- CISA’s latest advisory has also not gone unnoticed, for the group posted a response on June 30, 2023, stating: “A small Sudanese group with limited capabilities forced ‘the most powerful government’ in the world to publish articles and tweets about our attacks.” (4)
https://oodaloop.com/archive/2023/06/30/new-hacking-group-takes-down-russian-telecom-satellite-in-support-of-prigozhins-wagner-group/
OODAcon 2023
https://oodaloop.com/archive/2023/02/21/ooda-almanac-2023-useful-observations-for-contemplating-the-future/
The OODA C-Suite Report: Operational Intelligence for Business Leaders
https://oodaloop.com/archive/2022/05/12/with-viasat-satellite-hack-officially-attributed-to-russia-by-us-and-eu-allies-what-next-for-satellite-security/
https://oodaloop.com/archive/2022/03/22/cyber-attack-against-satellite-calls-into-question-satellite-security/
https://oodaloop.com/archive/2022/04/18/four-urgent-actions-for-the-c-suite-to-prepare-for-high-end-cyberattacks/
https://oodaloop.com/archive/2022/02/25/anonymous-wages-war-on-russia/
https://oodaloop.com/archive/2021/12/14/when-in-the-gray-zone-with-vladamir-putin-in-ukraine-dod-and-ic-hybrid-warfare-innovation-will-prove-vital/
https://oodaloop.com/archive/2019/07/17/ooda-special-report-the-kinetic-potential-of-russian-cyber-war/
https://oodaloop.com/archive/2022/06/29/lessons-on-the-future-of-cyberwar-from-russia/
https://oodaloop.com/archive/2023/04/19/ukraine-is-a-master-class-in-cyber-defense-and-a-real-time-ai-accelerator/
https://oodaloop.com/archive/2023/03/24/after-meeting-in-moscow-will-xi-and-putin-combine-it-armies-and-ict-driven-hybrid-warfare-efforts-against-the-west/
https://oodaloop.com/archive/2023/01/04/time-to-reconsider-the-how-state-actors-are-defined-in-cyberspace/
https://oodaloop.com/archive/2022/10/05/russias-cyber-attacks-in-ukraine-is-less-about-testing-new-attacks-and-all-about-regime-survival/
https://oodaloop.com/archive/2023/01/05/ooda-loop-2022-space-and-the-future-of-national-security-and-cybersecurity/
https://oodaloop.com/archive/2022/06/13/optical-communications-innovation-and-laser-satellites-are-the-future-of-space-communications/
https://oodaloop.com/archive/2021/08/09/what-the-c-suite-needs-to-know-about-a-return-to-great-power-competition-and-dod-capabilities-per-the-congressional-research-service/
About the Author
Daniel Pereira
Daniel Pereira is research director at OODA. He is a foresight strategist, creative technologist, and an information communication technology (ICT) and digital media researcher with 20+ years of experience directing public/private partnerships and strategic innovation initiatives.
Subscribe to OODA Daily Pulse
The OODA Daily Pulse Report provides a detailed summary of the top cybersecurity, technology, and global risk stories of the day.
 Source: Sekoia
Source: Sekoia