Start your day with intelligence. Get The OODA Daily Pulse.
Start your day with intelligence. Get The OODA Daily Pulse.
Midway through 2023 – and the scale, volume and frequency of ransomware cyber incidents are setting off alerts left and right in our risk awareness and sensemaking research efforts. In this post, we spend some time with recent report on the severity of the global ransomware epidemic – Chainalysis reports that ransomware gangs have extorted $449 million this year alone – and a really insightful report from the Stanford Internet Observatory assessing the political motivations behind ransomware attacks.
Consider our recent analysis of the US State Department $10M Bounty on the Clop Ransomware Gang Responsible for the Ongoing MOVEit Zero-day Vulnerability Rampage and the fact that the City of Dallas, Over a Month After A Ransomware Attack, is Still not at Full Functionality.
It turns out, both events are part of a troubling, larger whole – as, over the July Fourth holiday period, a major Japanese port suspended operation following a ransomware attack: “A cybercrime group believed to be operating out of Russia hit the largest and busiest trading port in Japan with a ransomware attack.
The Port of Nagoya, which accounts for roughly 10% of Japan’s total trade volume and is responsible for handling some car exports for companies like Toyota, suspended its cargo operations Tuesday, including the loading and unloading of containers onto trailers following the incident.
Nagoya’s port authority told several Japanese media outlets that it plans to resume operations Thursday morning. Local residents observed temporary congestion of trailers at the port.” (1)
Just yesterday, services in a North Carolina town are unavailable after a ransomware attack: “Residents of Cornelius, North Carolina, are dealing with delayed or unavailable services after a ransomware attack earlier this week.
The town has a population of about 32,000 people and is a prominent suburb of Charlotte located on Lake Norman. Government officials said on the evening of July 11, they discovered a cybersecurity incident later determined to be a ransomware attack.
“The Technology Operations (TechOps) Department immediately severed on-site technology from the network in order to contain the threat and prevent its spread,” the town government said.” (2)
“The figure likely pales in comparison to the actual totals because the research only looks at cryptocurrency wallets being monitored…”
Ransomware gangs have operated at a near-record profit in the first six months of the year, extorting more than $449 million from victims, according to blockchain research firm Chainalysis. If the trends continue, ransomware groups are on pace to bring in nearly $900 million in 2023, only $40 million behind the peak of $939.9 million seen in 2021.
Eric Jardine, cybercrimes research lead at Chainalysis [says] that a number of factors are contributing to ransomware’s resurgence rather than one specific driver, including the return of “big game hunting” — where ransomware gangs target large corporations in the hopes of garnering massive ransoms.
Jardine added that the effects of the Russia-Ukraine War — which experts believe caused the relative dip in ransom earnings in 2022 — are largely fading away as ransomware gangs get back to their typical level of activity. Chainalysis noted that groups like Cuba ransomware were forced to pivot from attacks for financial gain to others involving espionage and Ukraine-specific targets.
“The conflict likely displaced ransomware operators and diverted them away from financially inspired cyber intrusions,” he said.
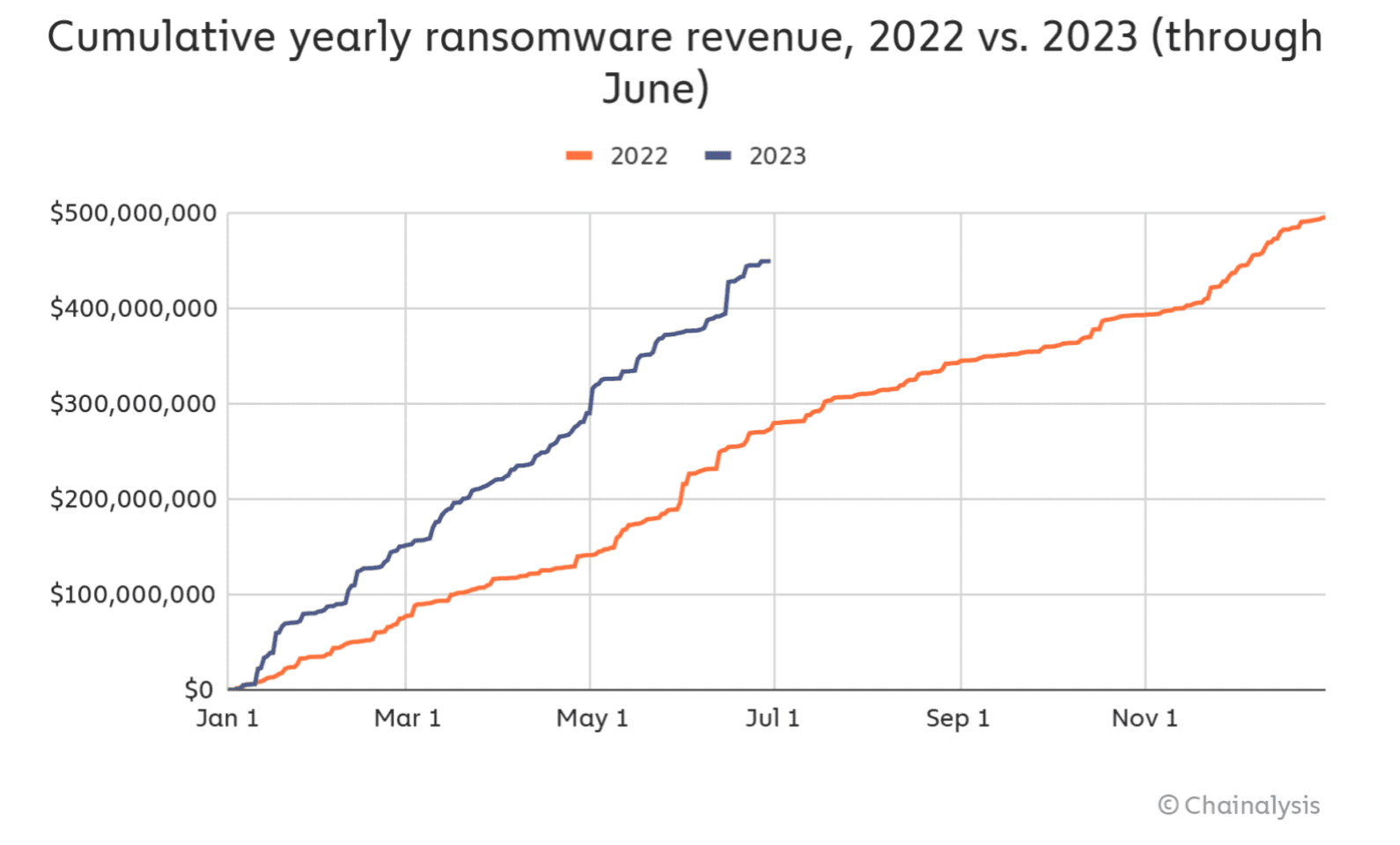
Ransomware revenue plummeted in 2022 compared to 2021, with fewer large scale attacks on massive companies. But the gangs have bounced back in 2023, increasing the number of attacks on “large, deep-pocketed organizations,” as well as smaller companies.
Charts from Chainalysis show increases both in the number of payments under $1,000 as well as payments over $100,000.
“The payment size distribution has also extended to include higher amounts compared to previous years. In other words, we’re seeing growth in ransomware payments at both ends of the spectrum,” the researchers said.
The company also tracked payment size based on ransomware group, finding that gangs like Dharma and Djvu saw average ransom payment sizes of $265 and $619 respectively.
Groups like Clop, AlphV/Black Cat and Black Basta saw average payments hovering above $750,000 and into the millions. Clop led the way with an average payment size of $1.73 million and a median payment size of $1.94 million. The gang is currently making waves globally with its attacks through the popular MOVEit software, allowing them to steal data and extort hundreds of organizations.
SafeBreach CISO Avishai Avivi said that while attacks on larger companies increased in 2023, he foresees these types of attacks eventually decreasing — as was seen last year — because more companies will realize the benefit of preparing for attacks in advance instead of spending millions to pay ransoms.
“As cyber insurance companies start declining coverage for ransomware-based losses, these organizations are more likely to invest in a more advanced security portfolio and validate that it can withstand even the newest ransomware attacks,” Avivi said.
The figures back up the findings of several other cybersecurity firms, which have seen increases in the number of reported attacks and victims posted to ransomware leaks sites.
![]()
The figures back up the findings of several other cybersecurity firms, which have seen increases in the number of reported attacks and victims posted to ransomware leaks sites. (3)
“Ransomware has emerged as the only cryptocurrency-based crime to grow in 2023, with cybercriminals extorting nearly $175.8 million more than they did a year ago, according to findings from Chainalysis. In contrast, crypto scams have pulled in 77% less revenue than they did through June of 2022, largely driven by the abrupt exit of VidiLook, which paid users VDL tokens in return for watching digital ads that could then be exchanged for large rewards. So have the inflows to illicit addresses associated with malware, darknet markets, child abuse material, and fraud shops.” (4)
The abstract from the researchers over at the Observatory:
Recent developments suggest possible links between some ransomware groups and the Russian government. We investigate this relationship by creating a dataset of ransomware victims and analyzing leaked communications from a major ransomware group.
Traditionally, ransomware attacks have been regarded as apolitical criminal activities. However, there is growing speculation about possible ties between Russia-based ransomware groups and the Kremlin. Our working paper aims to assess political motives behind ransomware attacks based on a newly gathered dataset of ransomware victims. Our findings challenge the notion that attack trends from Russia-based ransomware groups can be solely explained by financial motives.

Images show the “leak sites” of two dark web ransomware groups, Conti and Grief. Groups post about their victims on these sites as part of the extortion process. We have blurred victims’ identifying information to protect their privacy.
To construct the dataset, we collected information from 55 dark web leak sites, focusing on victims targeted by “double extortion” attacks. These attacks involve threatening to publish stolen data even after the victim has paid the ransom. The dataset comprises 4,194 victims from 55 ransomware groups, spanning the period from May 1, 2019, to April 30, 2022.
Our analysis reveals several notable patterns.
First: We observe an increase in the frequency of attacks by Russia-based ransomware groups leading up to elections in several major democracies, with no similar increase in attacks by groups based outside of Russia.
Second: Companies that withdrew from or suspended operations in Russia following the invasion of Ukraine were more likely to experience ransomware attacks in the months following the invasion, potentially indicating retaliatory motives.
Third: We find a decline in the number of daily ransomware attacks after the invasion, which could be attributed to Russia enlisting ransomware operators to support its cyber offensive against Ukraine.

Plot presents coefficients & confidence intervals for the effect of being in one of the three months before or after election period (the two weeks around an election) on the number of daily ransomware attacks by Russia-based (black) & other groups (gray)
We also analyzed over 60,000 leaked messages from a prominent Russia-based ransomware group called Conti. These communications show that Conti generally operated independently from the Russian state. However, they also reveal connections between Conti leaders and Russian government contacts and show cooperation on at least one state-backed cyber operation. The chats also reveal that group members believe the Russian government provides them and other groups with safe harbor.
Our data are consistent with a model where the Russian government maintains decentralized yet cooperative relations with Russia-based ransomware groups. The government offers safe harbor from prosecution in exchange for plausible deniability for attacks and access to skilled cyber actors. The Kremlin also benefits indirectly as groups primarily target victims in Western countries. Our findings suggest ransomware presents an international security threat in addition to functioning as a form of crime. (5)
To download the full report from the researchers at the Stanford Internet Observatory, see: Assessing the Political Motivations Behind Ransomware Attacks
https://oodaloop.com/archive/2023/04/04/cisas-pilot-ransomware-warning-system-and-pre-ransomware-notification-initiative/
https://oodaloop.com/archive/2023/07/06/the-continued-expansion-of-cyber-incidents-by-non-state-actors-in-the-war-in-europe/
https://oodaloop.com/archive/2023/03/21/how-to-manage-cyber-risk-as-a-board-director/