Start your day with intelligence. Get The OODA Daily Pulse.
Start your day with intelligence. Get The OODA Daily Pulse.
The exponential growth of the bioeconomy is all at once an opportunity for strategic competitive advantage and wrought with the perils of unintended consequences wrought by broad data security and cybersecurity vulnerabilities. A scraping incident last week at Genetic Testing Company 23andMe (resulting in the leak of data in the form of a ‘for sale’ offering on a cybercriminal forum) sheds light on these emerging threat vectors.
As reported by The Record:
23andMe scraping incident leaked data on 1.3 million users of Ashkenazi and Chinese descent. Here’s what you need to know:
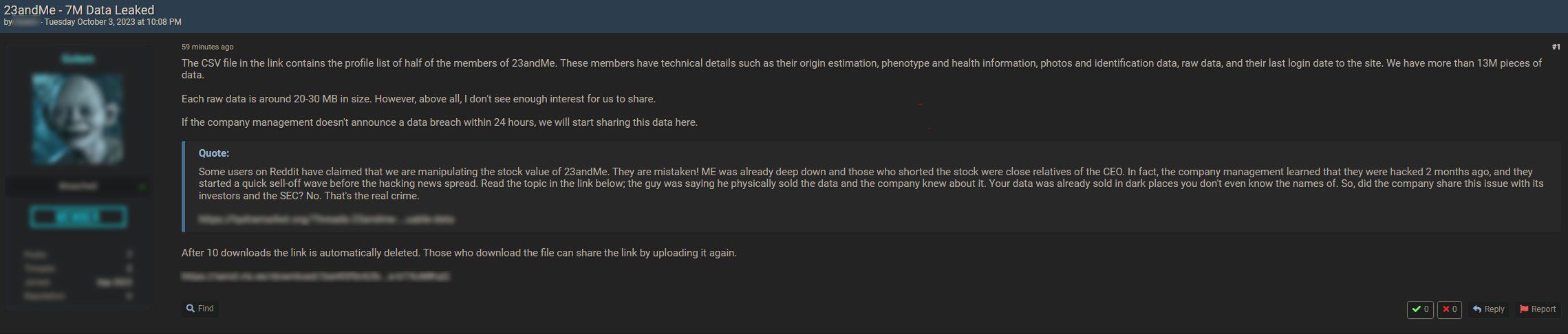
A screenshot from the posting of 23andMe data on the BreachForums site.
Image Source: The Record
The regulatory landscape for genetic testing companies in the United States and internationally is complex and constantly evolving due to the rapid advancements in genetic technology, ethical considerations, and the need to balance innovation with consumer protection. Here is a general overview of the regulatory climate for genetic testing companies in the United States and internationally:
United States
FDA Regulation: The U.S. Food and Drug Administration (FDA) oversees genetic tests, particularly those offered directly to consumers (DTC). In recent years, the FDA has been working on establishing a regulatory framework for DTC genetic tests, ensuring their accuracy and reliability.
CLIA Certification: Laboratories conducting genetic testing must be certified under the Clinical Laboratory Improvement Amendments (CLIA) program, which ensures the quality and accuracy of laboratory testing.
Genetic Information Nondiscrimination Act (GINA): GINA prohibits discrimination by health insurers and employers based on genetic information. This act provides some protection for individuals undergoing genetic testing.
From The Record: “The security policies of genetic testing companies like 23andMe have faced scrutiny from regulators in recent weeks. Three weeks ago, genetic testing firm 1Health.io agreed to pay the Federal Trade Commission (FTC) a $75,000 fine to resolve allegations that it failed to secure sensitive genetic and health data, retroactively overhauled its privacy policy without notifying and obtaining consent from customers whose data it had obtained, and tricked customers about their ability to delete their data.”
International
European Union (EU) – General Data Protection Regulation (GDPR): GDPR regulates the processing of personal data, including genetic data, within the EU and the European Economic Area (EEA). Companies handling genetic data must comply with strict data protection standards.
Canada – Personal Information Protection and Electronic Documents Act (PIPEDA): PIPEDA governs the collection, use, and disclosure of personal information, including genetic information, by private sector organizations in Canada.
United Kingdom – Data Protection Act 2018: The Data Protection Act 2018, aligned with the GDPR, governs the processing of genetic data in the UK.
Australia – Privacy Act 1988: The Privacy Act covers genetic information and imposes obligations on entities handling personal information, including genetic data, to comply with Australian Privacy Principles (APPs).
Ethical Concerns: The ethical use of genetic data, including issues related to consent, data security, and potential misuse of genetic information, is a significant concern globally.
Data Security: Genetic data is highly sensitive, and companies must implement robust security measures to protect this information from unauthorized access and breaches.
International Data Transfer: Companies operating internationally must navigate regulations related to the cross-border transfer of genetic data, ensuring compliance with data protection laws in different jurisdictions.
Informed Consent: Ensuring that individuals undergoing genetic testing fully understand the implications of the test and providing clear, informed consent is a critical ethical and regulatory consideration.
Emerging Technologies: Regulatory bodies must continuously adapt to advancements in genetic technologies, such as CRISPR gene editing, ensuring that these technologies are used responsibly and ethically.
Our analysis of the December 2021 hack of Ohio-based DNA Diagnostics Center (DDC) includes a discussion of the potential for the weaponization of large-scale genomic data, biotechnological datasets, or the acquisition of PPI related to a person’s genome or biotechnology-based information of patients (en mass) through a cyberattack (which would not only compromise the privacy of individuals, but would compromise the privacy of every relative of those individuals and every descendant of those individuals through eternity), includign a discussion of the potential for these types of unintended consequences emerging from biotechnology innovation and
In 2021, we reported on the annual findings from the UK’s The National Cyber Security Centre (NCSC), a part of Government Communications Headquarters (GCHQ), in which they highlight the type of cyber threat activity they have seen evolve over the last year (which overall has become more professional and strategic in their estimation) and is eerily similar to the cybercriminal behavior of the DDC and 23andMe hack:
“Organised crime groups spend time conducting in-depth reconnaissance on their targeted victims. They will identify exploitable cyber security weaknesses. They will use spoofing and spearphishing to masquerade as employees to get access to the networks they need. They will look for the business-critical files to encrypt and hold hostage. They may identify embarrassing or sensitive material that they can threaten to leak or sell to others. And they may even research to see if a potential victim’s insurance covers the payment of ransoms. This process can be painstaking and lengthy, but it means that, when they are ready to deploy, the effect of ransomware on an unprepared business is brutal.”
Consistent with this type of long term, strategic reconnaissance and espionage, it is as simple as this: the passwords which were acquired in the legacy database PII hack may well have been ported over as the access data on the new DDC system, in an effort at ‘ease of use’ for the new customers acquired by DDC in 2012 through M&A. This is a baseline process for most IT managers during a systems integration post-M&A. The intruders are probably already in DDC’s new company records, including access to genomic and biotechnology datasets.
As the details of the 23andMe scraping and leak emerge, similar threat vectors, infiltrations, and vulnerabilties may be discovered.
In our analysis of the Office of the Director of National Intelligence (DNI), National Counterintelligence and Security Center (NCSC) October 2021 report, “Protecting Critical and Emerging U.S. Technologies from Foreign Threats,” the NCSC defines the “The Bioeconomy” as economic activity “that is driven by research and innovation in biotechnology and is further enabled by the convergence of the life sciences and data sciences (e.g., informatics, high-performance/quantum computing, and telecommunications).
The NCSC points out societal benefits that include the future of food security, healthcare, climate sustainability, alternative fuels, material science innovation, and innovative new products and platforms for use in daily life. It is all very promising and exciting. But the 23andMe and DDC data hacks are representative of a type of activity which is part of a larger dystopian scenario:
“The powerful technologies harnessed by the bioeconomy can lead to national security and economic vulnerabilities. For example, biotechnology can be misused to create virulent pathogens that can target our food supply or even the human population. Genomic technology used to design disease therapies tailored to an individual also can be used to identify genetic vulnerabilities in a population. Large genetic databases that allow people’s ancestry to be revealed and crimes to be solved also can be misused for surveillance and societal repression.”
During the past decade, moreover, competition in the global bioeconomy has intensified. Foreign nations have stolen critical intellectual property, research, and know-how from the U.S. bioeconomy. And, as a result of some countries’ policies, an asymmetry exists in the way information is shared, whereby the ability of U.S.-based researchers to access and use such information is denied. Compounding the security challenges is that many existing legal frameworks focus on protecting finished intellectual property or licensed/patented products; whereas large bodies of data – such as patient health records or genetic sequence data – represent long-term, unrealized development of products and applications.”
Opportunities for advantage will be created by the exponential disruption of the industrial base (including that of defense) coupled with exponential biotechnology innovation to build the bioeconomy of the future. The creation of this technology and the business ecosystem of the future is already underway. This innovation is accelerating at this crazy pace – with what we’re able to achieve with CRISPR-type technologies, new therapies, and our understanding of disease. It will be incredibly disruptive.
There have been groundbreaking advancements in genetic engineering and new medical technologies are poised to disrupt the dialogue on health, ethics, global security, and the future of humanity, including disruptive technologies such as the revolutionary CRISPR gene-editing tool, breakthroughs in synthetic biology like Xenobots, and the emergence of exponential medical treatments that demonstrate rapid adoption properties.
In an effort to understand the risks and opportunities in this exponential industry sector by taking a look at a seminal case study by the Blockchain Research Institute on the future of patients owning and controlling their medical data – all on the blockchain. This research is also part of our current series on the Future of Blockchain.
Corporate Board Accountability for Cyber Risks: With a combination of market forces, regulatory changes, and strategic shifts, corporate boards and their directors are now accountable for cyber risks in their firms. See: Corporate Directors and Risk
Geopolitical-Cyber Risk Nexus: The interconnectivity brought by the Internet has made regional issues affect global cyberspace. Now, every significant event has cyber implications, making it imperative for leaders to recognize and act upon the symbiosis between geopolitical and cyber risks. See The Cyber Threat
Ransomware’s Rapid Evolution: Ransomware technology and its associated criminal business models have seen significant advancements. This has culminated in a heightened threat level, resembling a pandemic in its reach and impact. Yet, there are strategies available for threat mitigation. See: Ransomware, and update.
Challenges in Cyber “Net Assessment”: While leaders have long tried to gauge both cyber risk and security, actionable metrics remain elusive. Current metrics mainly determine if a system can be compromised, without guaranteeing its invulnerability. It’s imperative not just to develop action plans against risks but to contextualize the state of cybersecurity concerning cyber threats. Despite its importance, achieving a reliable net assessment is increasingly challenging due to the pervasive nature of modern technology. See: Cyber Threat
Proactive Mitigation of Cyber Threats: The relentless nature of cyber adversaries, whether they are criminals or nation-states, necessitates proactive measures. It’s crucial to remember that cybersecurity isn’t solely the responsibility of the IT department or the CISO – it’s a collective effort that involves the entire leadership. Relying solely on governmental actions isn’t advised given its inconsistent approach towards aiding industries in risk reduction. See: Cyber Defenses
The Necessity of Continuous Vigilance in Cybersecurity: The consistent warnings from the FBI and CISA concerning cybersecurity signal potential large-scale threats. Cybersecurity demands 24/7 attention, even on holidays. Ensuring team endurance and preventing burnout by allocating rest periods are imperative. See: Continuous Vigilance