Start your day with intelligence. Get The OODA Daily Pulse.
Start your day with intelligence. Get The OODA Daily Pulse.
Featured Image Source: Defending Ukraine: Early Lessons from the Cyber War (microsoft.com)
Last week, Microsoft released a report with an assessment of the cyber lessons learned in Ukraine since the inception of the conflict. A collaboration between Microsoft threat intelligence and data science teams, the report’s goals and conclusions are described in an Editor’s Note as:
Brad Smith, President and Vice-Chair of Microsoft, went with a non-traditional approach to corporate communications by opening his forward to the report with a brief march through the role and history of military technology:
“The recorded history of every war typically includes an account of the first shots fired and who witnessed them. Each account provides a glimpse not just into the start of a war, but the nature of the era in which people lived.
Historians who discuss the first shots in America’s Civil War in 1861 typically describe guns, cannons, and sailing ships around a fort near Charleston, South Carolina.
Events spiraled toward the launch of World War I in 1914 when terrorists in plain view on a city street in Sarajevo used grenades and a pistol to assassinate the archduke of the Austrian-Hungarian Empire.
It would take until the Nuremberg war trials to fully understand what happened near the Polish border 25 years later. In 1939, Nazi SS troops dressed in Polish uniforms and staged an attack against a German radio station. Adolf Hitler cited such attacks to justify a blitzkrieg invasion that combined tanks, planes, and troops to overrun Polish cities and civilians.
Each of these incidents also provides an account of the technology of the time — technology that would play a role in the war that ensued and the lives of the people who lived through it.
The war in Ukraine follows this pattern. The Russian military poured across the Ukrainian border on February 24, 2022, with a combination of troops, tanks, aircraft, and cruise missiles. But the first shots were in fact fired hours before when the calendar still said February 23. They involved a cyberweapon called “Foxblade” that was launched against computers in Ukraine. Reflecting the technology of our time, those among the first to observe the attack were half a world away, working in the United States in Redmond, Washington.
As much as anything, this captures the importance of stepping back and taking stock of the first several months of the war in Ukraine, which has been devastating for the country in terms of destruction and loss of life, including innocent civilians.
While no one can predict how long this war will last, it’s already apparent that it reflects a trend witnessed in other major conflicts over the past two centuries. Countries wage wars using the latest technology, and the wars themselves accelerate technological change. It’s therefore important to continually assess the impact of the war on the development and use of technology.
The Russian invasion relies in part on a cyber strategy that includes at least three distinct and sometimes coordinated efforts:
This report provides an update and analysis on each of these areas and the coordination among them. It also offers ideas about how to better counter these threats in this war and beyond, with new opportunities for governments and the private sector to work better together.” (1)
A brilliant Forward by Mr. Smith and his team over at Microsoft. On to the report…
Section 1 of the report itemizes the efforts by Ukrainians to mitigate the risk to their data infrastructure. In a stroke of just-in-time strategy and luck:
“Prior to the war, Ukraine had a longstanding Data Protection Law prohibiting government authorities from processing and storing data in the public cloud. This meant that the country’s public-sector digital infrastructure was run locally on servers physically located within the country’s borders. A week before the Russian invasion, the Ukrainian government was running entirely on servers located within government buildings—locations that were vulnerable to missile attacks and artillery bombardment.
Ukraine’s Minister of Digital Transformation, Mykhailo Fedorov, and his colleagues in Parliament recognized the need to address this vulnerability. On February 17, just days before Russian troops invaded, Ukraine’s Parliament took action to amend its data protection law to allow government data to move off existing on-premises servers and into the public cloud. This in effect enabled it to “evacuate” critical government data outside the country and into data centers across Europe.
Several tech companies rallied to help. At Microsoft, we witnessed and supported the speed required for this transition. Within 10 weeks, Ukraine’s Ministry of Digital Transformation and more than 90 chief digital transformation officers across the Ukrainian government worked with the company to transfer to the cloud many of the central government’s most important digital operations and data. Microsoft has committed at no charge a total of $107 million of technology services to support this effort, which has reached 20 ministries and more than 100 state agencies and state-owned enterprises. (In total, Microsoft has provided $239 million in financial and technology assistance to support Ukraine, including support for the government, businesses, nonprofits, and humanitarian assistance for refugees.)
Fedorov’s urgency was prophetic. An early target of Russian missile attacks was a Ukrainian government data center. And as discussed further below, the Russian military has targeted the government’s on-premises computer networks with its destructive cyber “wiper” attacks. One reason these kinetic and cyberattacks have had limited operational impact is because digital operations and data have been disbursed into the public cloud.” (2)
We have reported here at OODA Loop on the impressive, newfound private sector collaboration and leadership in areas of cyber attack incident reports with CISA and working with the FBI and SEC to bring innovative, impactful charges against cyber criminals and cyber gangs. Count this Microsoft effort described above amongst those activities which deserve acknowledgment and praise.
 Source: Microsoft
Source: Microsoft
“The war in Ukraine has pitted offensive cyberattacks that are invisible to the naked eye against advances in cybersecurity technologies and operations…some of the cyberattacks have succeeded in reaching and disabling their targets. But at a broader level, so far these attacks have failed strategically in disabling Ukraine’s defenses. While part of the reason lies in the disbursement of Ukrainian digital operations into the cloud, as discussed above, another reason has been the overall ability of cyber defenses to successfully defeat these attacks.
It’s important to take note of the destructive cyber tactics the Russian military has deployed in Ukraine. These have three facets:
 Source: Microsoft
Source: Microsoft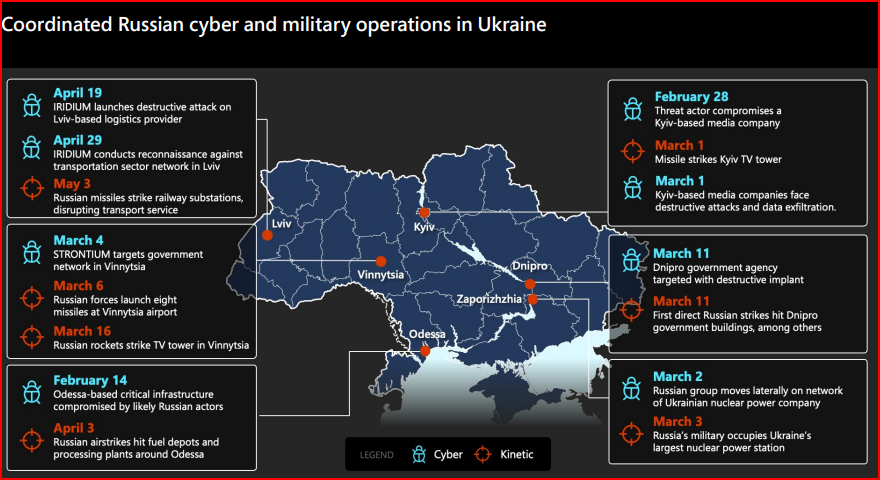 Source: Microsoft
Source: Microsoft
“It’s important to recognize that Russian cyber tactics in the war have been strategic and deliberate but are different from the 2017 NotPetya attack. To date, the Russians haven’t used destructive ‘wormable’ malware that can jump from one computer domain to another and thereby cross international borders to spread economic damage. Instead, they are designing attacks to stay within Ukraine. While Russia has been careful to confine its destructive malware to specific network domains located within Ukraine itself, these attacks are more sophisticated and widespread than many reports recognize.
But the more limited impact is attributable to other factors as well. Because cyberattacks are invisible to the naked eye, they tend to be perceived by the public and reported by journalists only when they succeed and computer networks stop operating. And, to date at least, cyber defenses and operations have withstood attacks far more often than they have failed.
Ultimately, all this illustrates three features that characterize the state of cybersecurity protection as we approach the second quarter of the 21st century:
 Source: Microsoft
Source: Microsoft
 Source: Microsoft
Source: Microsoft
“Perhaps more than anything, the lessons from Ukraine call for a coordinated and comprehensive multilateral and multistakeholder strategy to strengthen defenses against the full range of Russian cyber destructive, espionage, and influence operations. It’s perhaps too easy for those outside of Russia to view these three areas as falling into separate silos. But it’s helpful to recall the lessons that the British author and journalist Gillian Tett documented more broadly in her book “The Silo Effect.” Notably, when people put problems and issues in different categories, they more likely will fail to connect the dots between them. In this case, analytical fragmentation creates the risk of tunnel vision for different cyber defenses and creates opportunities for foreign adversaries to exploit the seams between disconnected defensive efforts.
In fact, new advances in the defense of all these cyber threats will depend on some common tenets and, at least at a high level, a common strategy:” (2)
 Source: Microsoft
Source: Microsoft
Brad Smith and the team at Microsoft that created this report also offer their conclusions and recommendations:
“The cyber aspects of the current war extend far beyond Ukraine and reflect the unique nature of cyberspace. When countries send code into battle, their weapons move at the speed of light. The internet’s global pathways mean that cyber activities erase much of the longstanding protection provided by borders, walls, and oceans. And the internet itself, unlike land, sea, and the air, is a human creation that relies on a combination of public and private- sector ownership, operation, and protection.
This in turn requires a new form of collective defense. This war pits Russia, a major cyber-power, not just against an alliance of countries. The cyber defense of Ukraine relies critically on a coalition of countries, companies, and NGOs.
The world can now start to assess the early and relative strengths and weaknesses of offensive and defensive cyber operations. Where are collective defenses successfully thwarting attacks and where are they falling short? What types of technological innovations are taking place? And critically, what steps are needed to effectively defend against cyberattacks in the future? Among other things, it’s important to base these assessments on accurate data and not be misled into an unwarranted sense of tranquility from the external perception that the cyberwar in Ukraine has not been as destructive as some feared.
This report offers five conclusions that come from the war’s first four months:
First, defense against a military invasion now requires for most countries the ability to disburse and distribute digital operations and data assets across borders and into other countries. Russia not surprisingly targeted Ukraine’s governmental data center in an early cruise missile attack, and other “on-premise” servers similarly were vulnerable to attacks by conventional weapons. Russia also targeted its destructive “wiper” attacks at on-premises computer networks. But Ukraine’s government has successfully sustained its civil and military operations by acting quickly to disburse its digital infrastructure into the public cloud, where it has been hosted in data centers across Europe. This has involved urgent and extraordinary steps from across the tech sector, including by Microsoft. While the tech sector’s work has been vital, it’s also important to think about the longer-lasting lessons that come from these efforts.
Second, recent advances in cyber threat intelligence and end-point protection have helped Ukraine withstand a high percentage of destructive Russian cyberattacks. Because cyber activities are invisible to the naked eye, they are more difficult for journalists and even many military analysts to track. Microsoft has seen the Russian military launch multiple waves of destructive cyberattacks against 48 distinct Ukrainian agencies and enterprises. These have sought to penetrate network domains by initially comprising hundreds of computers and then spreading malware designed to destroy the software and data on thousands of others.
Third, as a coalition of countries has come together to defend Ukraine, Russian intelligence agencies have stepped up network penetration and espionage activities targeting allied governments outside Ukraine. At Microsoft we’ve detected Russian network intrusion efforts on 128 organizations in 42 countries outside Ukraine. While the United States has been Russia’s number one target, this activity has also prioritized Poland, where much of the logistical delivery of military and humanitarian assistance is being coordinated. Russian activities have also targeted Baltic countries, and during the past two months there has been an increase in similar activity targeting computer networks in Denmark, Norway, Finland, Sweden, and Turkey. We have also seen an increase in similar activity targeting the foreign ministries of other NATO countries.
Fourth, in coordination with these other cyber activities, Russian agencies are conducting global cyber-influence operations to support their war efforts. These combine tactics developed by the KGB over several decades with new digital technologies and the internet to give foreign influence operations a broader geographic reach, higher volume, more precise targeting, and greater speed and agility. Unfortunately, with sufficient planning and sophistication, these cyber-influence operations are well-positioned to take advantage of the longstanding openness of democratic societies and the public polarization that is characteristic of current times.
Finally, the lessons from Ukraine call for a coordinated and comprehensive strategy to strengthen defenses against the full range of cyber destructive, espionage, and influence operations. As the war in Ukraine illustrates, while there are differences among these threats, the Russian Government does not pursue them as separate efforts and we should not put them in separate analytical silos. In addition, defensive strategies must consider the coordination of these cyber operations with kinetic military operations, as witnessed in Ukraine.
New advances to thwart these cyber threats are needed, and they will depend on four common tenets and — at least at a high level — a common strategy. The first defensive tenet should recognize that Russian cyber threats are being advanced by a common set of actors inside and outside the Russian Government and rely on similar digital tactics. As a result, advances in digital technology, AI, and data will be needed to counter them. Reflecting this, a second tenet should recognize that unlike the traditional threats of the past, cyber responses must rely on greater public and private collaboration. A third tenet should embrace the need for close and common multilateral collaboration among governments to protect open and democratic societies. And a fourth and final defensive tenet should uphold free expression and avoid censorship in democratic societies, even as new steps are needed to address the full range of cyber threats that include cyber influence operations.
An effective response must build on these tenets with four strategic pillars. These should increase collective capabilities to better (1) detect, (2) defend against, (3) disrupt, and (4) deter foreign cyber threats. This approach is already reflected in many collective efforts to address destructive cyberattacks and cyber-based espionage. They also apply to the critical and ongoing work needed to address ransomware attacks. We now need a similar and comprehensive approach with new capabilities and defenses to combat Russian cyber influence operations.
As discussed in this report, the war in Ukraine provides not only lessons but a call to action for effective measures that will be vital to the protection of democracy’s future. As a company, we are committed to supporting these efforts, including through ongoing and new investments in technology, data, and partnerships that will support governments, companies, NGOs, and universities.” (1)
It should go without saying that tracking threats are critical to informing your actions. This includes reading our OODA Daily Pulse, which will give you insights into the nature of the threat and risks to business operations.
Use OODA Loop to improve your decision making in any competitive endeavor. Explore OODA Loop
The greatest determinant of your success will be the quality of your decisions. We examine frameworks for understanding and reducing risk while enabling opportunities. Topics include Black Swans, Gray Rhinos, Foresight, Strategy, Stratigames, Business Intelligence and Intelligent Enterprises. Leadership in the modern age is also a key topic in this domain. Explore Decision Intelligence
We track the rapidly changing world of technology with a focus on what leaders need to know to improve decision-making. The future of tech is being created now and we provide insights that enable optimized action based on the future of tech. We provide deep insights into Artificial Intelligence, Machine Learning, Cloud Computing, Quantum Computing, Security Technology, Space Technology. Explore Disruptive/Exponential Tech
Security and resiliency topics include geopolitical and cyber risk, cyber conflict, cyber diplomacy, cybersecurity, nation state conflict, non-nation state conflict, global health, international crime, supply chain and terrorism. Explore Security and Resiliency
The OODA community includes a broad group of decision-makers, analysts, entrepreneurs, government leaders and tech creators. Interact with and learn from your peers via online monthly meetings, OODA Salons, the OODAcast, in-person conferences and an online forum. For the most sensitive discussions interact with executive leaders via a closed Wickr channel. The community also has access to a member only video library. Explore The OODA Community