Start your day with intelligence. Get The OODA Daily Pulse.
Start your day with intelligence. Get The OODA Daily Pulse.
Featured Image Source: Kaspersky.com
Congratulations to @threatinsight researcher @aRtAGGI for presenting his research today at @CYBERWARCON, which links #Leviathan #TA423 #RedLadon campaigns against offshore energy companies in the #SouthChinaSea to kinetic maritime operations conducted by the Chinese Coast Guard! pic.twitter.com/rUTYX640uI
— Threat Insight (@threatinsight) November 10, 2022
I am beyond excited to drop new research today with my coauthor @cyberoverdrive on TA423/RedLadon (aka Leviathan). It’s rare for @threatinsight to partner with others but Sveva and @PwC Global Threat Intelligence Team are among the rarest talents. 1/3🧵https://t.co/WsPTQfl9E7
— Digital_Monet (@aRtAGGI) August 30, 2022
From the description of the presentation “Rising Tide Redux” at CYBERWARCON 2022, which was held recently in-person (and virtual) in Arlington, VA:
Leviathan, a Chinese APT [advanced persistent threat] actor and contractor known to support the Chinese Ministry of State Security, is targeting the supply chains of naval defense and energy exploration entities active in the South China Sea. According to continuous phishing operations identified by Proofpoint since mid-2021, this group has continued their campaigns without interruption since the US DOJ indictment in July of that year.
This talk will examine two specific use cases from June 2021 and March 2022, which support an exploration of how a known reliable MSS contractor, per the details of the historic US DOJ indictment, may now support intelligence requirements tied to the deployment of kinetic naval intervention in areas of active dispute between the Chinese Communist Party and other nations in Southeast Asia and Oceania. Further by examining the timeline of these attacks, this talk will present a previously undisclosed link to a Chinese State service branch actively carrying out maritime patrols and harassing energy projects in the South China Sea.
Michael August Raggi is a Staff Threat Research Engineer at Proofpoint. Previously, he has worked as a Cyber Intelligence Analyst at BAE Systems and in the financial services sector as a Cyber Threat Analyst. Michael’s historic publications have focused on APT targeting against the US critical infrastructure sector, recent operations conducted during the Russia-Ukraine conflict, and repeated targeting of Tibetan dissidents by threat actors aligned with the Chinese State. His primary focus is tracking APT adversaries in the APAC region and developing analyst tools to automate the detection of top-tier threat actors. (1)
Proofpoint’s Threat Research Team details a recent cyber espionage campaign targeting entities globally and conducted by a threat actor publicly which was attributed in 2021 by multiple governments and was the focus of a 2021 indictment by the US Department of Justice. The targets of this recent campaign spanned Australia, Malaysia, and Europe, as well as entities that operate in the South China Sea. Proofpoint’s research has been assisted by the PwC Threat Intelligence team to provide the information security community with a comprehensive view of the threat activity described.
Proofpoint and PwC Threat Intelligence have jointly identified a cyber espionage campaign, active since April 2022 through June, delivering the ScanBox exploitation framework to targets who visit a malicious domain posing as an Australian news website. The joint efforts of Proofpoint and PwC researchers provide a moderate confidence assessment that recent campaigns targeting the federal government, energy, and manufacturing sectors globally may represent recent efforts by TA423 / Red Ladon. Activity that overlaps with this threat actor has been publicly referred to in governmental indictments as “APT40” and “Leviathan.” This blog analyzes the structure and capabilities of the sample of ScanBox and the plugins identified in this campaign. It also correlates this campaign and its observed victimology with previous campaigns conducted by TA423 / Red Ladon which leveraged RTF template injection.
The [research] details:
TA423 / Red Ladon: TA423 / Red Ladon is a China-based, espionage-motivated threat actor that has been active since 2013, targeting a variety of organizations in response to political events in the Asia-Pacific region, with a focus on the South China Sea. Targeted organizations include defense contractors, manufacturers, universities, government agencies, legal firms involved in diplomatic disputes, and foreign companies involved with Australasian policy or South China Sea operations.
Beginning on 12 April 2022, and continuing through mid-June 2022, Proofpoint identified several waves of a phishing campaign resulting in the execution of the ScanBox reconnaissance framework, in part based on intelligence shared by PwC Threat Intelligence related to ongoing ScanBox activity. The phishing campaign involved URLs delivered in phishing emails, which redirected victims to a malicious website posing as an Australian news media outlet. The website’s landing page delivered a JavaScript ScanBox malware payload to selected targets. In historic instances, ScanBox has been delivered from websites that were the victim of strategic web compromise (SWC) attacks with legitimate sites being injected with malicious JavaScript code. In this instance, the threat actor controls the malicious site and delivers malicious code to unsuspecting users.
A ScanBox Primer: ScanBox, detailed in open source as early as 2014 by AlienVault, is a JavaScript-based web reconnaissance and exploitation framework which allows threat actors to profile victims, and to deliver further malware to selected targets of interest. PwC Threat Intelligence assesses it is highly likely that ScanBox is shared privately amongst multiple China-based threat actors.
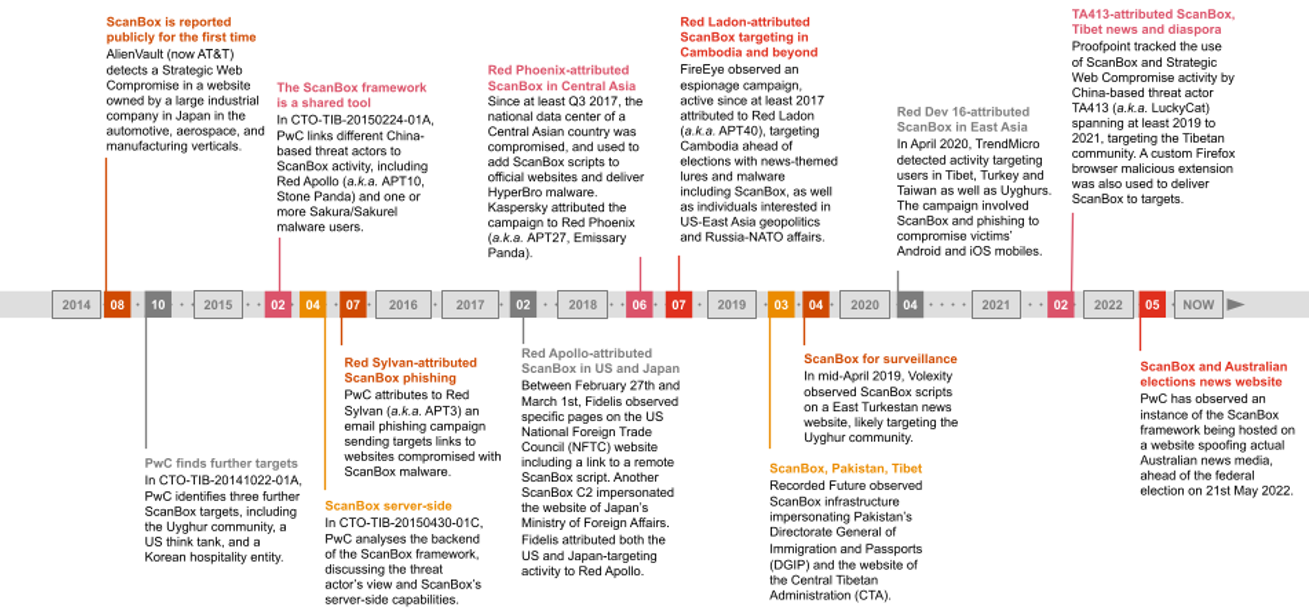
Figure 1. A timeline of activity involving ScanBox since 2014 to May 2022
The following China-based threat actors have been observed using ScanBox:
TA423 / Red Ladon’s 2018 ScanBox activity targeting Cambodia involved domains masquerading as news websites and targeted high profile government entities, including the National Election Commission. One of the ScanBox server domains used in that campaign, mlcdailynews[.]com, hosted several articles about Cambodian affairs and US and East Asia relations, for which contents were copied from legitimate publications (Khmer Post, Asia Times, Reuters, Associated Press). These were likely used as lures in phishing emails to convince targets to follow malicious links to the actor-controlled ScanBox domain.
The April 2022 to June 2022 ScanBox campaign primarily targeted:
This demonstrated the comingling of targets involved in Australian governmental affairs as well as offshore energy production in the South China Sea. Proofpoint previously observed similar targeting in June 2021 by TA423 / Red Ladon, wherein the threat actor would deliver a downloader in DLL format via RTF template injection. The campaign showed a consistency of victimology spanning thirteen months and bridging diverse phishing tactics, techniques, and procedures (TTPs).
The ScanBox-related phishing campaigns identified in April through June 2022 originated from Gmail and Outlook email addresses which Proofpoint assess with moderate confidence were created by the threat actor, and utilized a variety of subjects including “Sick Leave,” “User Research,” and “Request Cooperation.” The threat actor would frequently pose as an employee of the fictional media publication “Australian Morning News”, providing a URL to the malicious domain and soliciting targets to view its website or share research content that the website would publish.
In emails, the threat actor claimed to be starting a “humble news website” (sic) and solicited user feedback while providing a link to australianmorningnews[.]com. While this is not impersonating an existing Australian media publication, it does copy content from legitimate news publications (including the BBC and Sky News) which was then displayed when victims navigated to the website.
Upon clicking the link and redirecting to the site, visitors were served the ScanBox framework. The impersonation of a fictional media publication local to targets of interest is a tactic that Proofpoint and PwC Threat Intelligence had previously observed being used in historic TA423 / Red Ladon ScanBox campaigns identified preceding the Cambodian elections in 2018. The content of the emails and the malicious URL technique reprised a technique previously observed in September 2021 TA423 / Red Ladon campaigns detailed later in this blog, in which the threat actor impersonated Australian media publications with its malware delivery infrastructure.
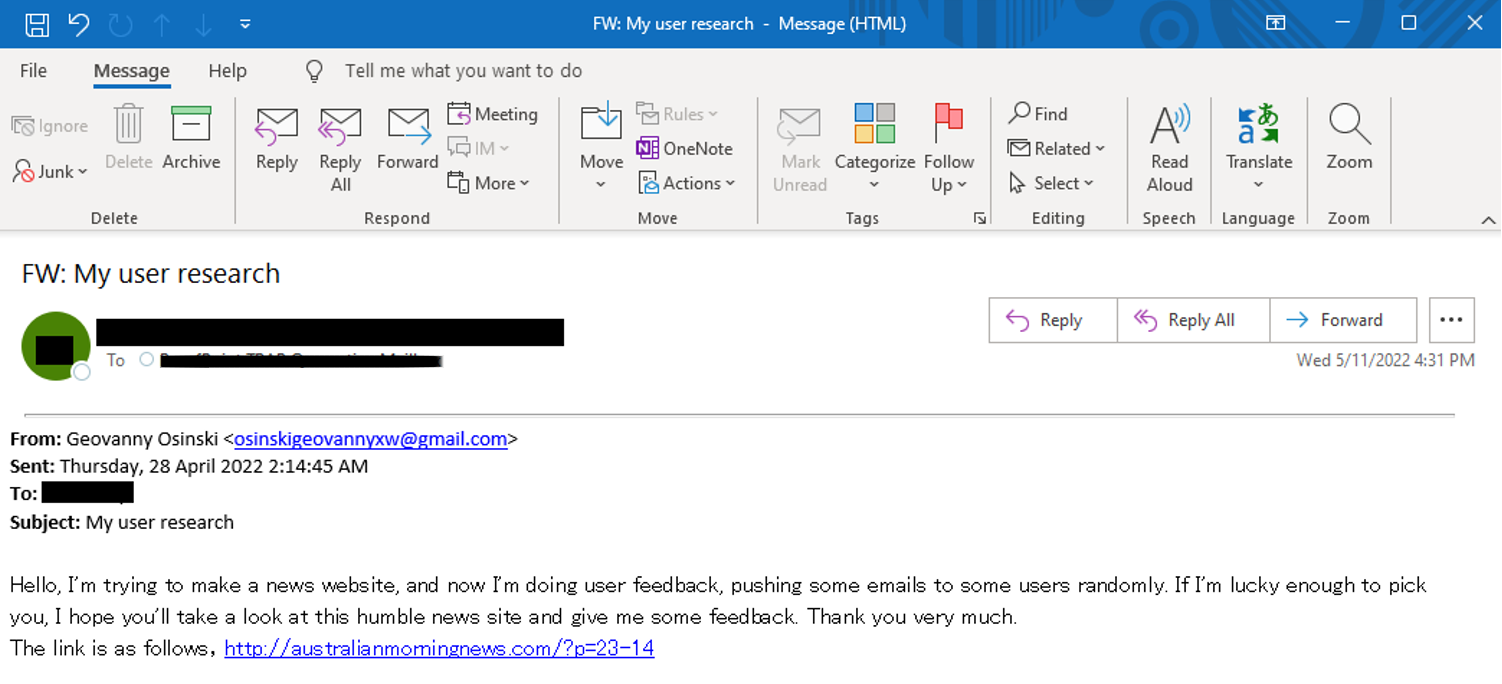 Figure 2. TA423 Phishing Emails 28 April 2022 and 1 June 2022
Figure 2. TA423 Phishing Emails 28 April 2022 and 1 June 2022
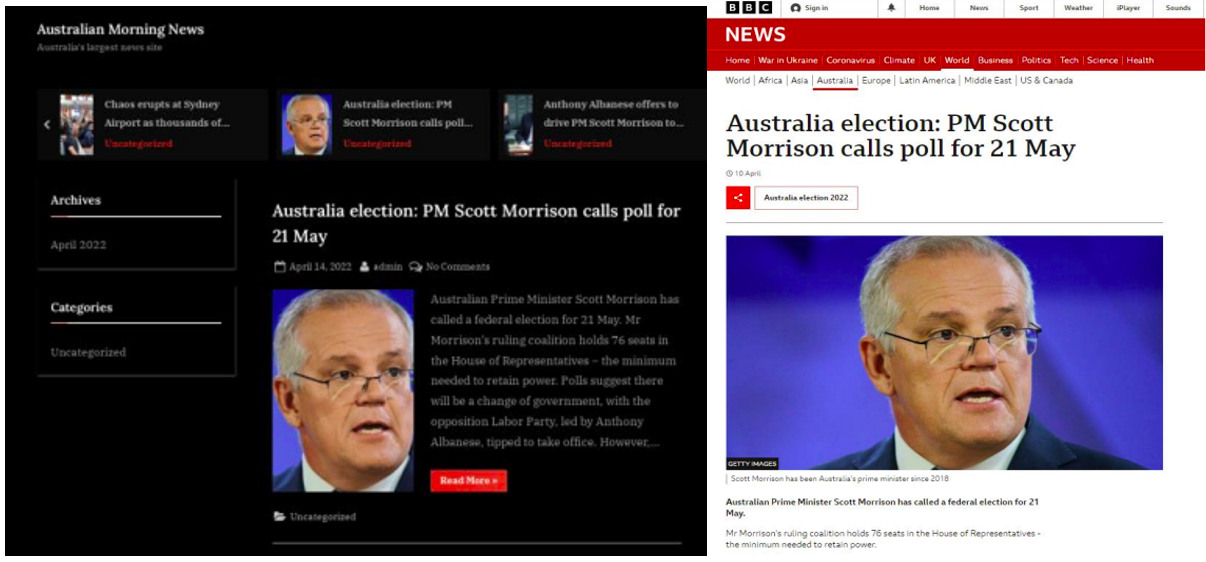
Figure 3. The homepage of australianmorningnews[.]com, posing as “Australia’s largest news site”. The same exact headline, picture, and text can be found in the BBC’s coverage.
An interesting commonality to earlier activity can be observed across several of the campaigns identified from April through May 2022. The malicious URLs provided in the emails also appear to use values that are customized for each target, although they all redirect to the same page and serve the same malicious payload. In one instance the threat actor was observed appending the URI extension “?p=23-<##>”. It appears that p=23 specifies the page value for landing page the user is redirected to, while the number string that follows it, e.g. the “11” in “?p=23-11”, appears to be a unique identifier for each recipient. Proofpoint had also observed customized URLs, and URL redirect destinations distinct for each target, in TA423’s earlier campaigns in March 2022. This may be an attempt by the threat actor to correlate traffic to its servers, which host the page infected by ScanBox malware, with custom user identifiers which targets received within the URLs via email:
Beginning in March 2021, Proofpoint began to observe a consistent pattern of targeting against entities based in Malaysia and Australia, as well as against entities that are involved in the operations and supply chain of offshore energy projects in the South China Sea. From June 2021 through May 2022, Proofpoint observed an ongoing phishing campaign which involved malicious RTF attachments weaponized through template injection. Additionally, this campaign made use of malicious URLs which delivered RTF template injection files. Both initial infection vectors delivered first-stage downloader malware to targets. The downloaders retrieved XOR-encoded versions of Meterpreter shellcode.
Throughout this campaign, Australian targets regularly included military academic institutions, as well as local and federal government, defense, and public health sectors. Malaysian targets included offshore drilling and deep-water energy exploration entities as well as global marketing and financial companies. Several global companies were also targeted that appear to relate to the global supply chains of offshore energy projects in the South China Sea. These included:
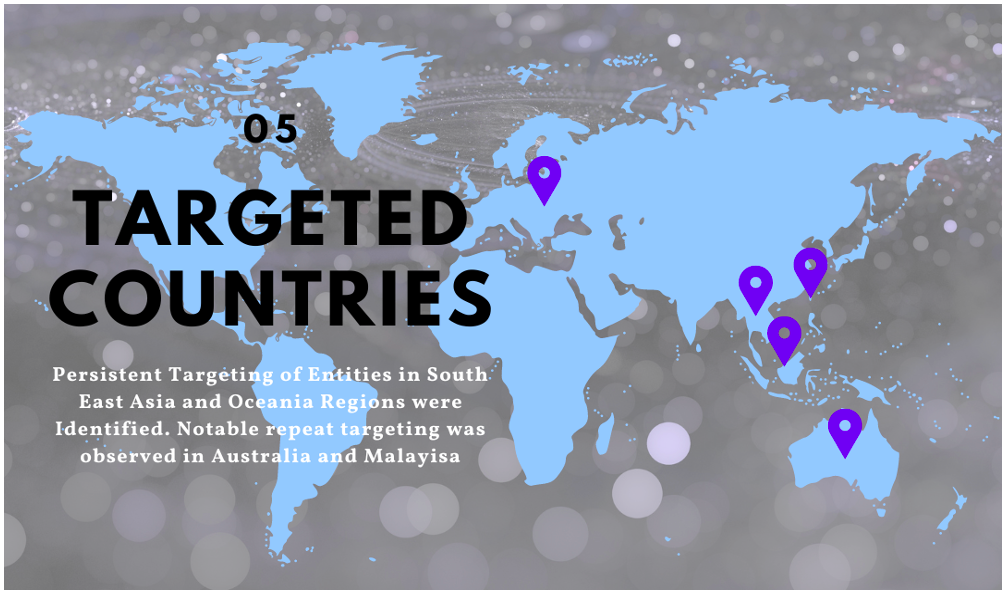 Figure 9. A Visualization of Targeted Countries
Figure 9. A Visualization of Targeted Countries
Proofpoint assesses with moderate confidence that the campaigns were conducted by the China-based, espionage-motivated threat actor TA423, which PwC tracks as Red Ladon and which also overlaps with “Leviathan,” “GADOLINIUM,” and “APT40.”
This threat actor has demonstrated a consistent focus on entities involved with energy exploration in the South China Sea, in tandem with domestic Australian targets including defense and health care. Both the CopyPaste attacks targeting the Australian government in 2021, attributed publicly to TA423 / Red Ladon, and the threat actor’s historic focus on the South China Sea, align with the observed victimology of the long running campaign described in this blog. More distinctly, this threat actor has repeatedly targeted both Australian governmental and energy-related target sets within a single campaign over multiple years.
Finally, this threat actor has been observed using both ScanBox in a watering hole capacity as well as Meterpreter in intrusions within the geographic areas that this observed threat actor is currently operating.
On 2 June 2021 numerous emails were sent from a Gmail email address to several companies involved with deep water drilling, oil and petroleum exploration, and Australian Naval Defense. The emails used “COVID19 passport services in Australia” themes to deliver the aforementioned ZIP and RTF attachments that utilize RTF template injection to download a DLL stager and downloader payload leading to a Meterpreter payload.
Figure 11. RTF Template Injection Attachment titled “COVID-19 and passport services Australia.”
This campaign focused heavily on Malaysia, and specifically on companies that appear to be involved in either the engineering, extraction of natural gasses, or export of natural gas products from the Kasawari Gas Project off the coast of Malaysia. Specifically, four of the eight entities targeted by this campaign were associated directly with this project. Additional targets observed in this campaign were involved in Australian Defense universities, consumer healthcare in Australia, and large financial banking entities in Malaysia. A similar array of targeting across Australian domestic entities and organisations operating in the South China Sea was later observed in the May 2022 ScanBox campaign that was described in the Phase 3 phishing activity section of this publication.
In close temporal proximity to the cyber espionage campaigns targeting these entities, the Asia Maritime Transparency Initiative reported disruption at the project site stemming from Chinese Coast Guard Intervention. Proofpoint assesses with moderate confidence that this activity may be attributable to the threat actor TA423 / Red Ladon, which multiple reports assess to operate out of Hainan Island, China. A 2021 indictment by the US Department of Justice assessed that TA423 / Red Ladon provides long-running support to the Hainan Province Ministry of State Security (MSS). One of TA423’s longest running areas of responsibility is assessed to include the South China Sea, with the US Department of Justice indictment indicating that the threat actor has historically focused on intellectual property related to naval technology developed by federally-funded defense contractors globally. This indictment also explicitly included the mention of the existence of the Yulin Naval Base which has been stated to be located on Hainan Island.
While a direct correlation cannot be drawn between the cyber espionage campaign targeting entities involved with the site and portions of its supply chain in the days directly preceding kinetic naval intervention, the historic targeting focus of TA423 / Red Ladon and the subsequent naval intervention may suggest that this project in the South China Sea was highly likely an area of priority interest for the threat actor.
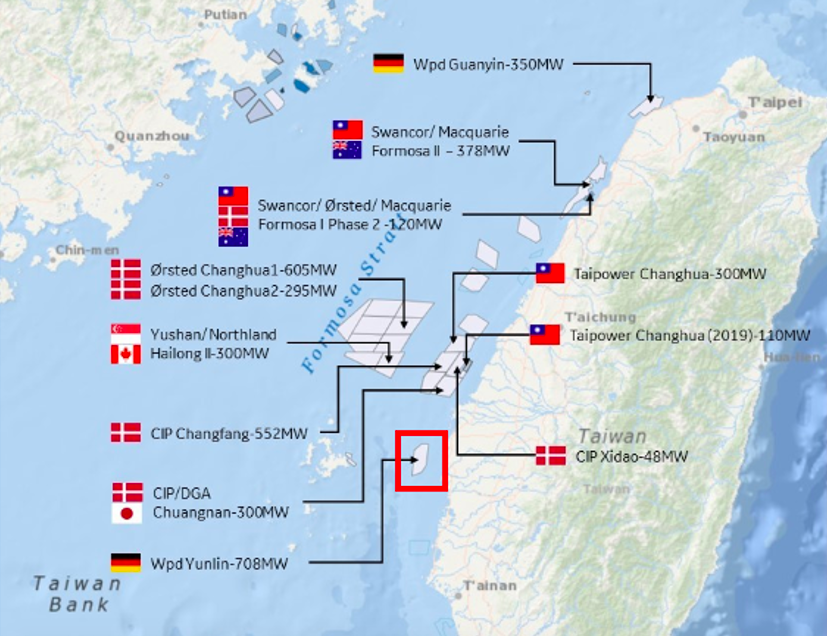
On 24th, 28th, and 29th March 2022, Proofpoint observed phishing activity leveraging RTF template injection that targeted a European manufacturer of heavy equipment utilized in the installation of an offshore windfarm in the Strait of Taiwan. Specifically, the manufacturer targeted was a key supplier of equipment for entities involved in the construction of the Yunlin Offshore Windfarm. This is a project which begun in 2020 and was projected to be completed in 2022. However, the project began to encounter construction delays which resulted in several major contractors terminating contracts and leaving the project unfinished between November 2021 and February 2022. This offshore energy project resumed in late April 2022.
The dates of the observed phishing activity align with the period between 2nd February 2022 and 28th April 2022 where the project’s future was uncertain. The targeting of supply chain entities by TA423 during this period of project uncertainty is notable, since the group has previously targeted projects in the South China Sea during key moments in their development timeline.
Overall, Proofpoint and PwC collectively expect TA423 / Red Ladon to continue pursuing its intelligence-gathering and espionage mission primarily targeting countries in the South China Sea, as well as further intrusions in Australia, Europe, and the United States. (2)
For the full Proofpoint blog post: Rising Tide: Chasing the Currents of Espionage in the South China Sea
It should go without saying that tracking threats are critical to inform your actions. This includes reading our OODA Daily Pulse, which will give you insights into the nature of the threat and risks to business operations.
Use OODA Loop to improve your decision-making in any competitive endeavor. Explore OODA Loop
The greatest determinant of your success will be the quality of your decisions. We examine frameworks for understanding and reducing risk while enabling opportunities. Topics include Black Swans, Gray Rhinos, Foresight, Strategy, Strategies, Business Intelligence, and Intelligent Enterprises. Leadership in the modern age is also a key topic in this domain. Explore Decision Intelligence
We track the rapidly changing world of technology with a focus on what leaders need to know to improve decision-making. The future of tech is being created now and we provide insights that enable optimized action based on the future of tech. We provide deep insights into Artificial Intelligence, Machine Learning, Cloud Computing, Quantum Computing, Security Technology, and Space Technology. Explore Disruptive/Exponential Tech
Security and resiliency topics include geopolitical and cyber risk, cyber conflict, cyber diplomacy, cybersecurity, nation-state conflict, non-nation-state conflict, global health, international crime, supply chain, and terrorism. Explore Security and Resiliency
The OODA community includes a broad group of decision-makers, analysts, entrepreneurs, government leaders, and tech creators. Interact with and learn from your peers via online monthly meetings, OODA Salons, the OODAcast, in-person conferences, and an online forum. For the most sensitive discussions interact with executive leaders via a closed Wickr channel. The community also has access to a member-only video library. Explore The OODA Community.